
On September 20, 2022, a London-based cryptocurrency market maker, Wintermute, was hacked, resulting in a loss of $160 million. Our analysis at Numen Cyber Technology shows that the hackers likely cracked the company’s wallet’s private key.
This incident highlights the need for not just preventing contract loopholes, but also securing the supply chain platforms and wallets.
How did they crack the wallet’s private key?
The hack was enabled by the use of a tool called Profanity, which generates addresses with custom characters. On September 15th, 1inch Network warned investors that addresses generated through this tool were particularly vulnerable as their private keys could easily be cracked through a brute force attack. The hackers used this principle in their attack:
- Obtain a public key from a vanity address (recover it from the transaction signature).
- Expand it deterministically to 2 million public keys.
- Conduct decrements until they reach the seed public key.
The 1inch Network official article link can be found here.

Details of the attack process
Attacker address:
https://etherscan.io/address/0xe74b28c2eAe8679e3cCc3a94d5d0dE83CCB84705
Attacker contract address:
https://etherscan.io/address/0x0248f752802b2cfb4373cc0c3bc3964429385c26
Wintermute stolen wallet address:
https://etherscan.io/address/0x0000000fe6a514a32abdcdfcc076c85243de899b
Wintermute Stolen Contract Address:
https://etherscan.io/address/0x00000000ae347930bd1e7b0f35588b92280f9e75
Attack Methodology
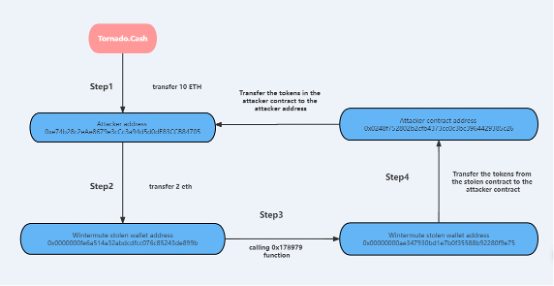
- The hacker first transferred 10 ETH from Tornado.Cash to their own wallet address (0xe74b28c2eAe8679e3cCc3a94d5d0dE83CCB84705).

2. The hacker then transferred 2 ETH from their own wallet address to the hacked Wintermute wallet address (0x0000000fe6a514a32abdcdfcc076c85243de899b) as a fee for calling the contract.
3. The hacker then used the hacked Wintermute wallet (0x0000000fe6a514a32abdcdfcc076c85243de899b) to call the 0x178979ae function in the hacked Wintermute contract (0x00000000ae347930bd1e7b0f35588b92280f9e75) to transfer tokens to the attacker’s contract (0x0248f752802b2cfb4373cc0c3bc3964429385c26). There were many transfer operations, and only the first transfer was 5890 WETH.

4. Through the bytecode analysis of the hacked Wintermute contract, it was found that the 0x178979ae function call has permission to verify, and the address 0x0000000fe6a514a32abdcdfcc076c85243de899b has this permission. So the hacker used this address to transfer the tokens under the contract.

Wintermute official response
TThe founder of Wintermute tweeted that they were hacked for about $160 million, but that their Cefi and OTC operations were not affected. He also stated that they are still solvent and they intend to handle the incident as a white hat attack, in the hopes that the attacker will come forward.

Wallet security related events
Recently, a wallet theft on the Solana public chain occurred, with the assets in the user’s wallet transferred without their knowledge, resulting in a loss of over $6 million. Numen Cyber Labs analyzed the details of the theft and determined that the wallet’s private key was leaked.
Verdict
This follows a warning issued by 1Inch that addresses generated by the Profanity tool have security risks. However, wallet security issues were not taken seriously by users and project parties until the Wintermute hack occurred, which gained widespread attention.
Numen Cyber Labs recommends users who store their assets in addresses generated by the Profanity tool to transfer them to a safe wallet address as soon as possible. We also recommend that the Wintermute project party remove the contract permission address and replace it with a secure wallet address.
We remind users and project parties to conduct proper security testing and seek proper protection for their wallets and to seek out third-party companies for security services if necessary.
Relevant Incidents
Speaking of Wintermute, you may also recall an incident from June of this year regarding a replay attack.
Hacking of 20 Million OP Tokens:
During the launch of the OP token, Optimism contracted Wintermute to provide liquidity services for OP tokens in the secondary market. As part of the agreement, Optimism provided 20 million OP tokens to Wintermute.
To receive the assets, Wintermute provided a multi-signature contract address on Ethereum (L1) (0x4f3a120E72C76c22ae802D129F599BFDbc31cb81), but this address was not deployed on Optimism (L2). When Optimism transferred 20 million OP Tokens in three transactions, Wintermute had no control over these tokens, which caught the attention of hackers.
By replaying Ethereum (L1) transactions on Optimism (L2), the hackers created the address 0x4f3a120e72c76c22ae802d129f599bfdbc31cb81, gaining control of 2,000 OP tokens.
Replay Attack Relevant Events
Several days ago, a replay attack occurred on the Gnosis Omni Bridge. The hacker transferred 200 WETH through the Omni Bridge, then used the same input data to perform the same attack on the ETHW chain, resulting in the theft of an additional 200 ETHW.
This was primarily due to the project not properly verifying the Chain ID during the process, and instead relying on a fixed storage value.
Summary
After analyzing these attack events, Numen Cyber Labs believes that contracts should be created using secure functions. Ethereum was upgraded from Proof-of-Work to Proof-of-Stake, and as a result, the compatibility and security of some projects were exposed. We remind project parties and users to prioritize security detection and protection for projects and assets.
If you wish to audit and ensure that your projects are free from exploits such as these, please reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!
This blog was originally published on our Medium Account.


