
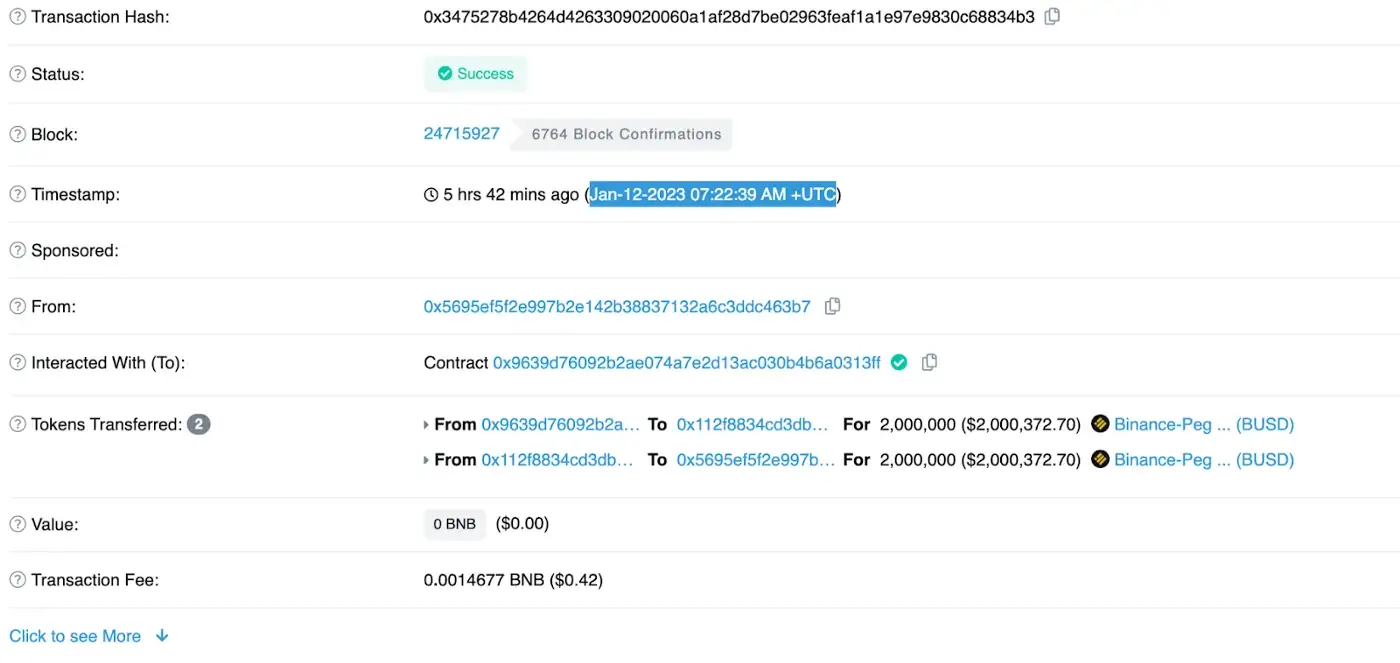
Jan-12–2023 07:22:39 AM +UTC, according to NUMEN on-chain monitoring, the CirculateBUSD project has been drained by the contract creator (AKA Rugpull), causing a loss of $2.27 million.
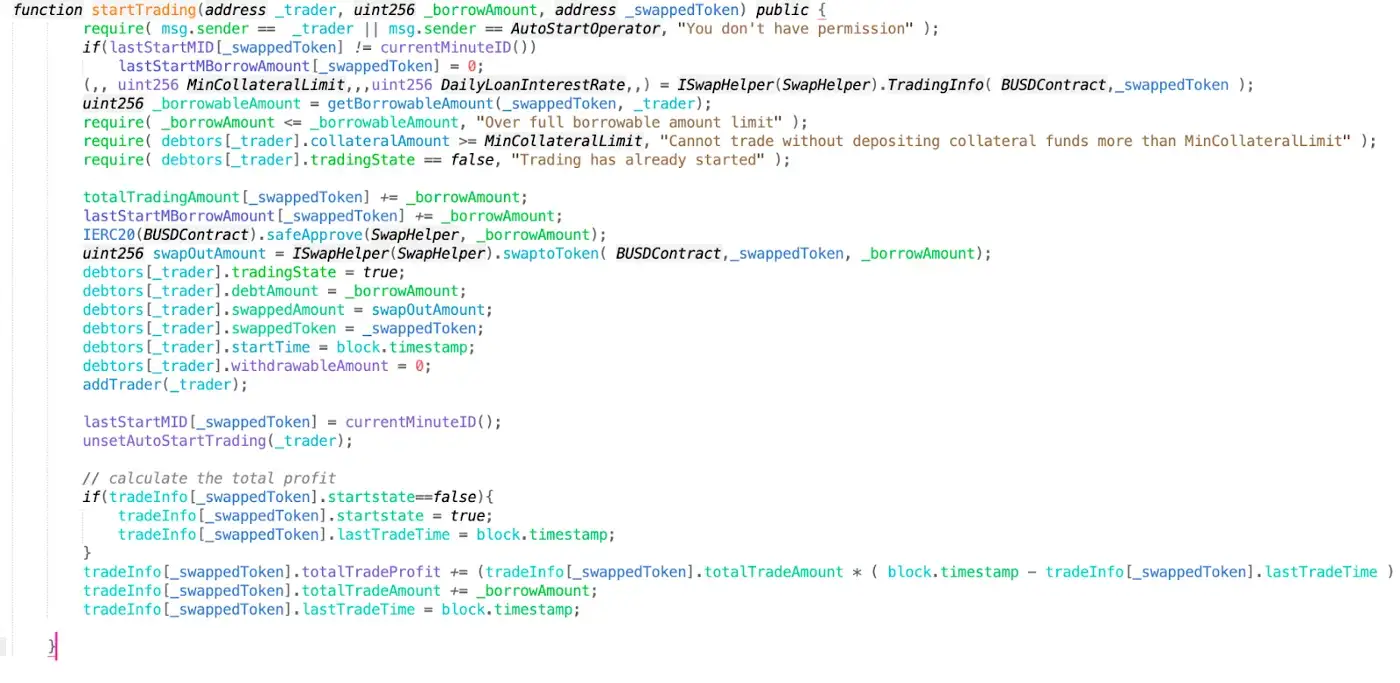
The fund transfer of this project is mainly because the administrator calls CirculateBUSD.startTrading, and the main judgment parameter in startTrading is the value returned by the non-open source contract SwapHelper.TradingInfo set by the administrator, and then calls SwapHelper.swaptoToken to transfer funds.
Transaction:https://bscscan.com/tx/0x3475278b4264d4263309020060a1af28d7be02963feaf1a1e97e9830c68834b3
Rugpull Analysis:
Firstly, it calls contract startTrading (https://bscscan.com/address/0x9639d76092b2ae074a7e2d13ac030b4b6a0313ff), and inside the function, the SwapHelper contract’s TradingInfo function is called, with the following details. The code is as follows.
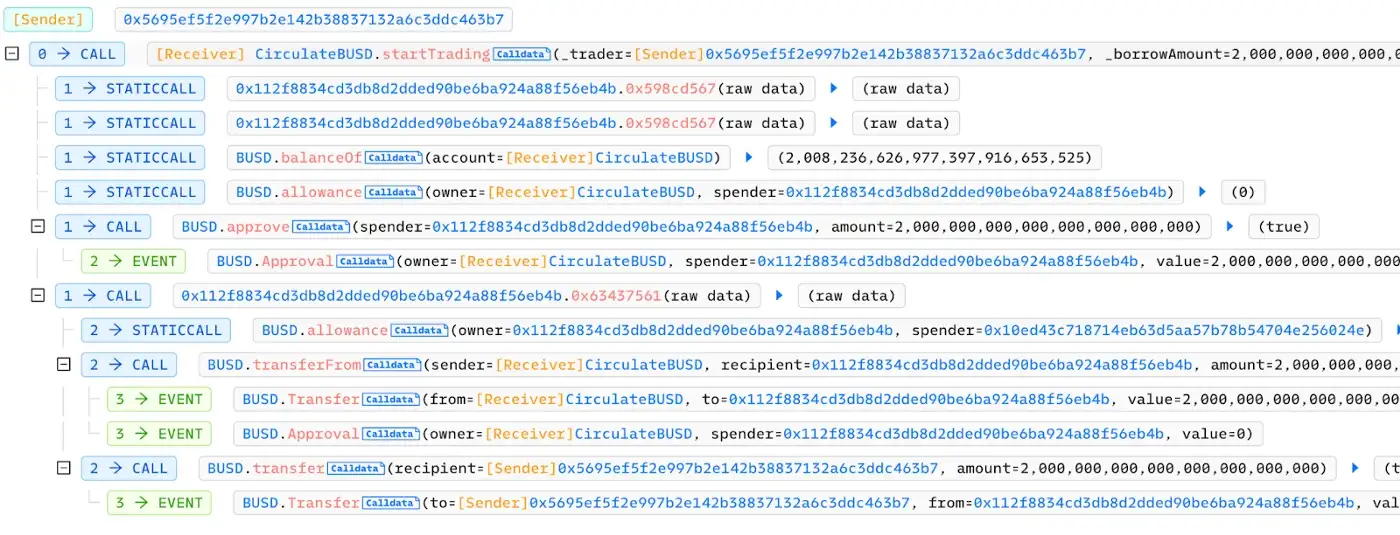
The above figure is the call stack of tx. Combined with the code we can see that TradingInfo inside only some static calls, the key problem is not in this function. Continuing with the analysis, we found that the call stack is corresponding to the approve operation and safeapprove.
Then SwapHelper’s swaptoToken function was called, which was found to be a key function in combination with the call stack, and the transfer transaction was executed in this call. The SwapHelper contract is not open source as found by the on-chain information at the following address.
https://bscscan.com/address/0x112f8834cd3db8d2dded90be6ba924a88f56eb4b#code
Trying to reverse the analysis, we firstly locate the function signature 0x63437561.
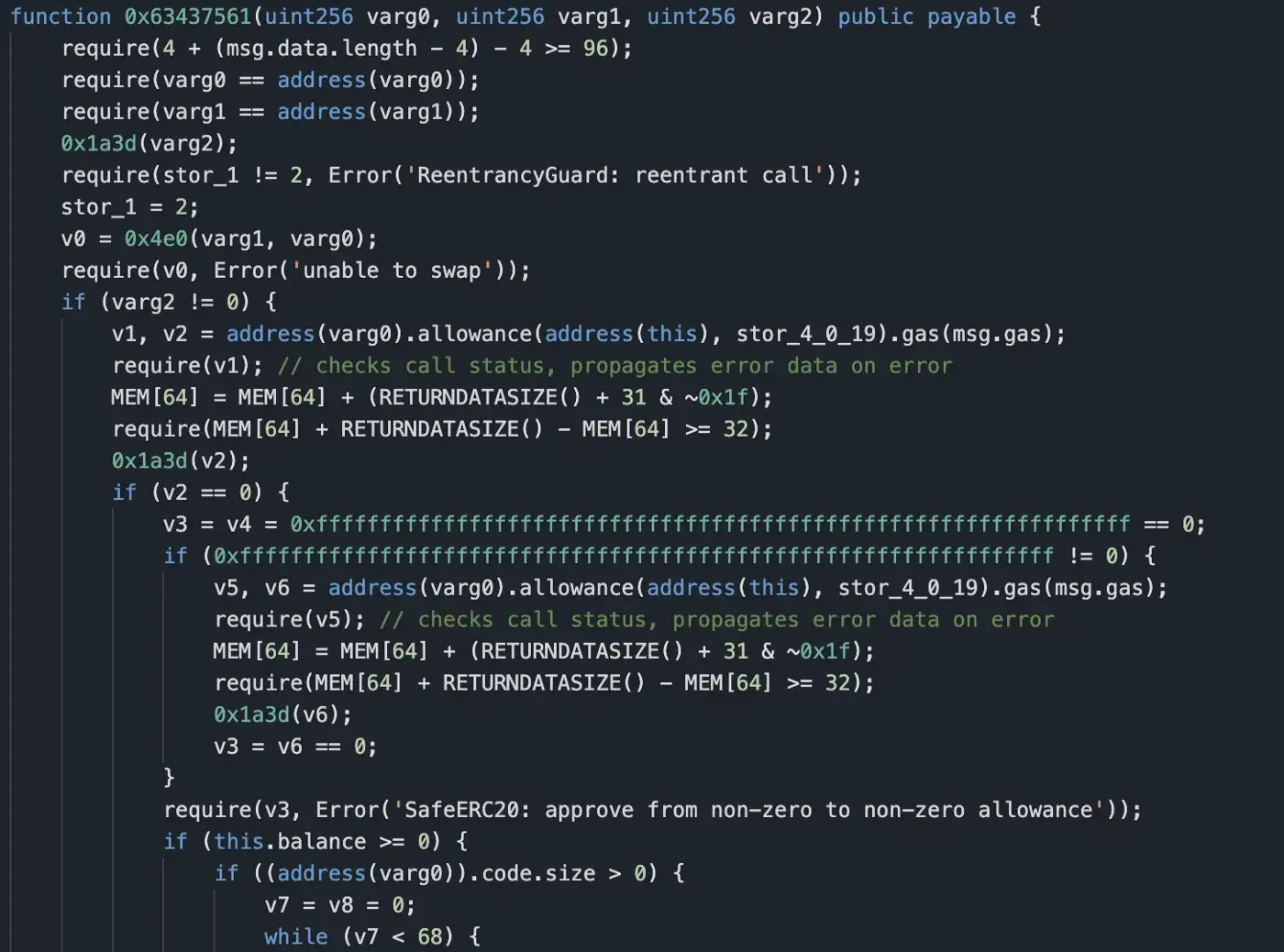
Subsequently, we located this function after decompiling and tried to find keywords such as transfer because you see that the call stack triggers a transfer.
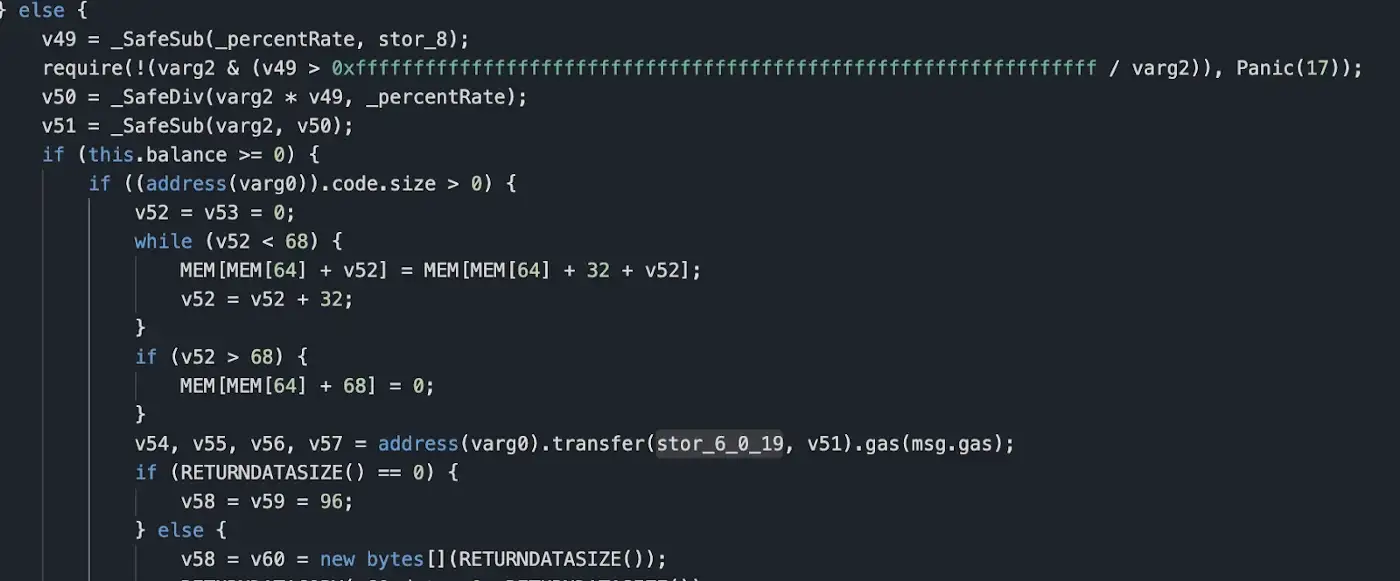
So locate this branch of the function, first stor_6_0_19, and read that part out first.
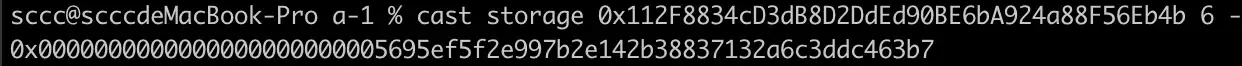
At this point , the transfer to address was obtained, 0x0000000000000000000000005695ef5f2e997b2e142b38837132a6c3ddc463b7, which was found to be the same as the transfer to address of the call stack.
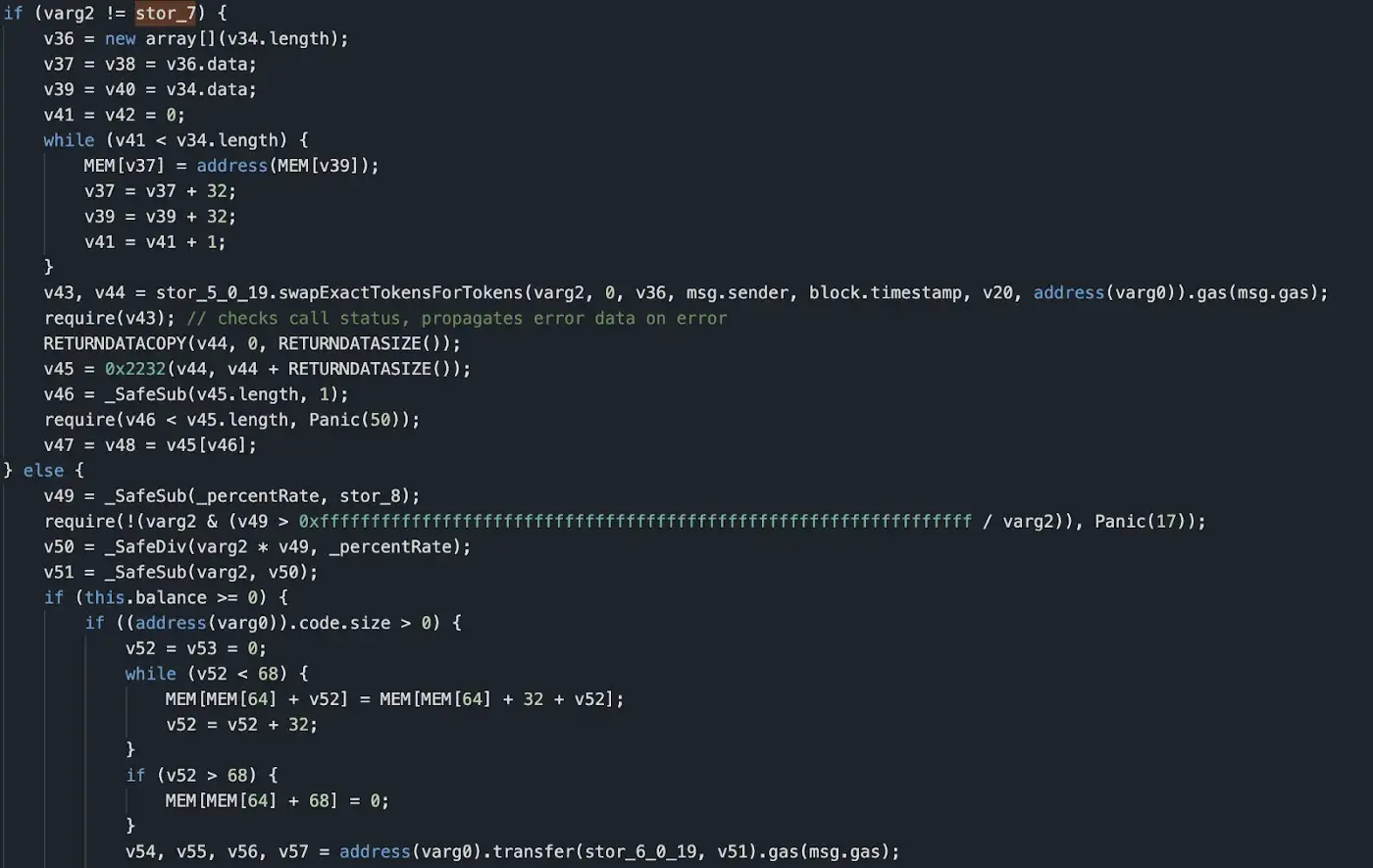
When we carefully analyzed the if and else branches of this function, we found that if it meets the if condition, it will do a normal redemption . Because the slot to get stor5 is 0x00000000000000000000000010ed43c718714eb63d5aa57b78b54704e256024e, this contract is pancakerouter. backdoor function in the else branch, as long as the parameters passed in and stor7 slot stored value equal to trigger.
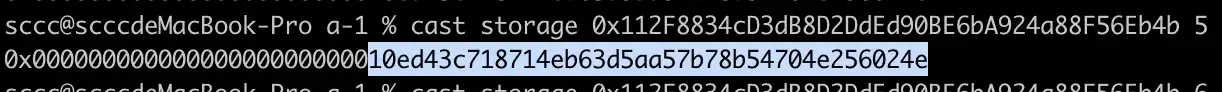
Below function is to modify the value of the slot 7 position, and the call permission is only owned by the contract owner.
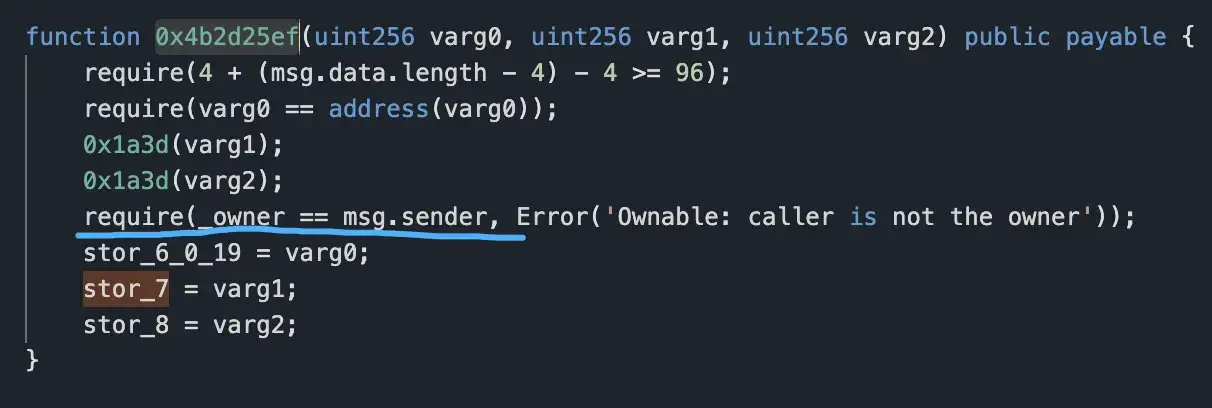
The above analysis is enough to determine that this is a project-side rugpull incident.
Summary
Numen Cyber Labs remind users that when making investment decisions, it’s necessary to conduct security audits on the project’s contracts. There may be functions in the unverified contract where the project’s authority is too large or directly affects the safety of the user’s assets. The problems with this project are just the tip of the iceberg of the entire blockchain ecosystem. When users invest and project parties develop projects, they must conduct security audits on the code.
Should you wish to audit and ensure that your projects are free from exploits such as these, reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!
This blog was originally published on our Medium Account.


