Preface
Apache ShenYu is a Java native API Gateway for service proxy, protocol conversion and API governance.
Description
Numen Cyber Labs vulnerability researchers have discovered an SSRF vulnerability in Apache ShenYu< version 2.6.
CVE ID
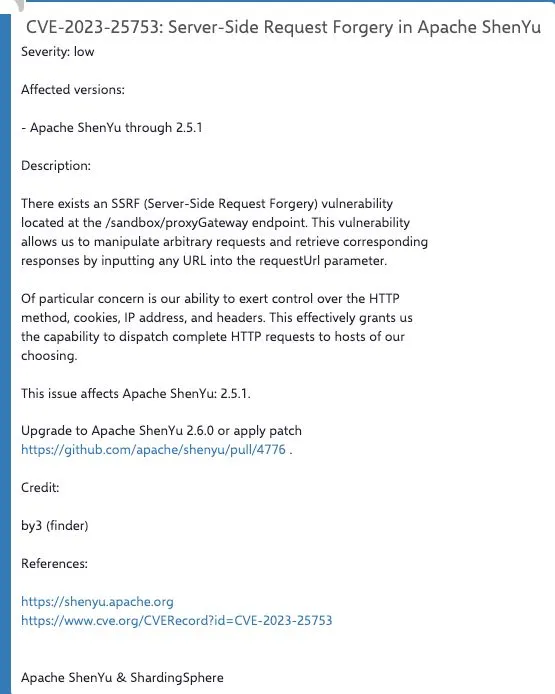
Impacts version
< 2.6
Analysis
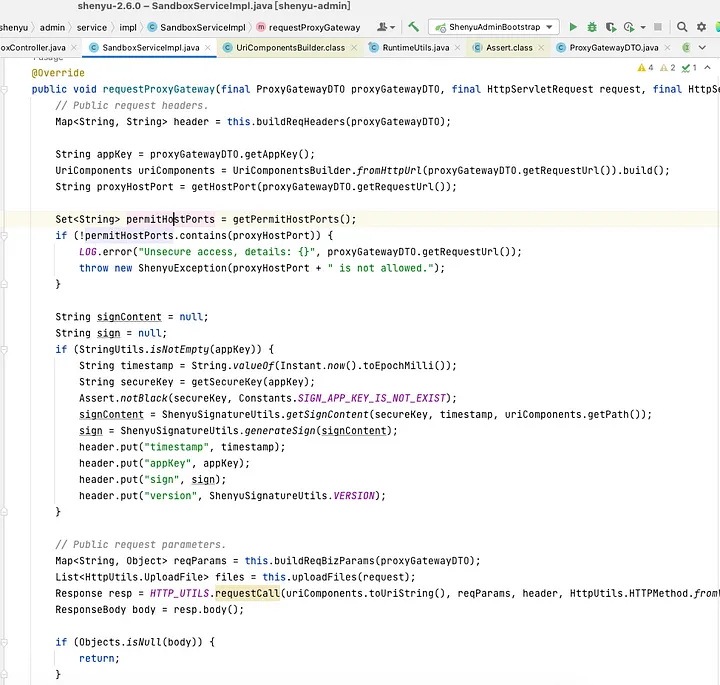
org.apache.shenyu.admin.controller.SandboxController#proxyGateway receives proxyGatewayDTO, calls requestProxyGateway method
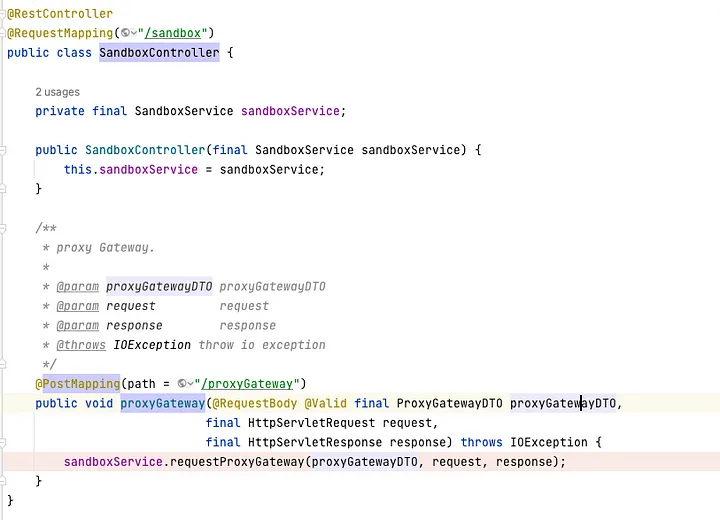
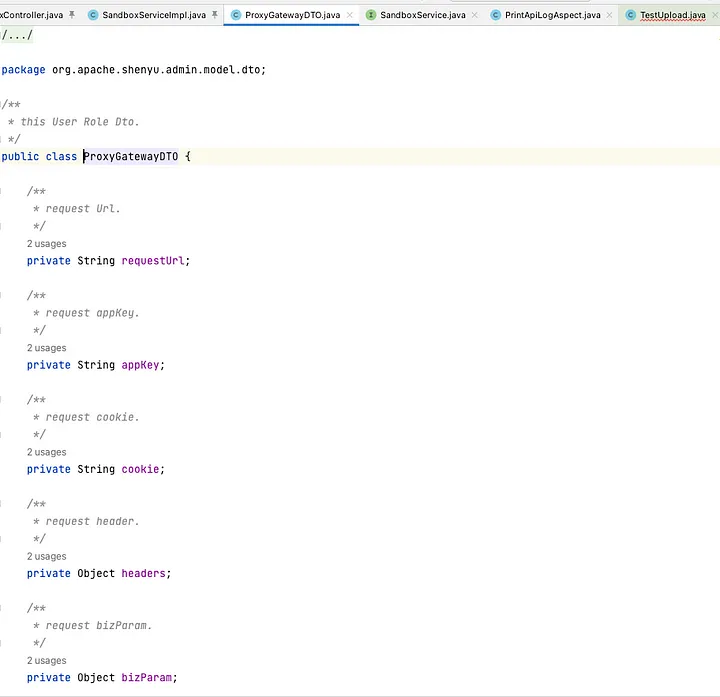
ProxyGatewayDTO has requestUrl, cookie, headers, httpMethod parameters
requestProxyGateway method gets the parameters in the ProxyGatewayDTO, call org.apache.shenyu.admin.utils.HttpUtils#requestCall to launch the request
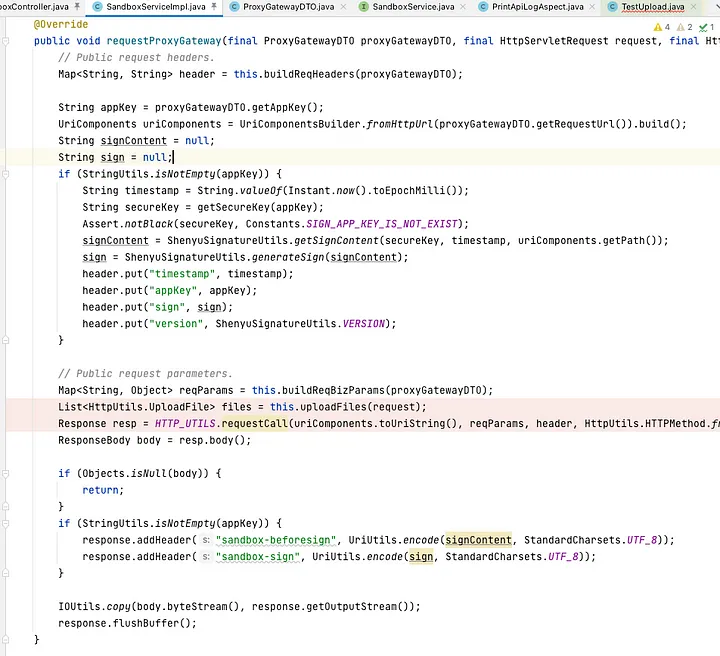
requestCall is used to build the http request.
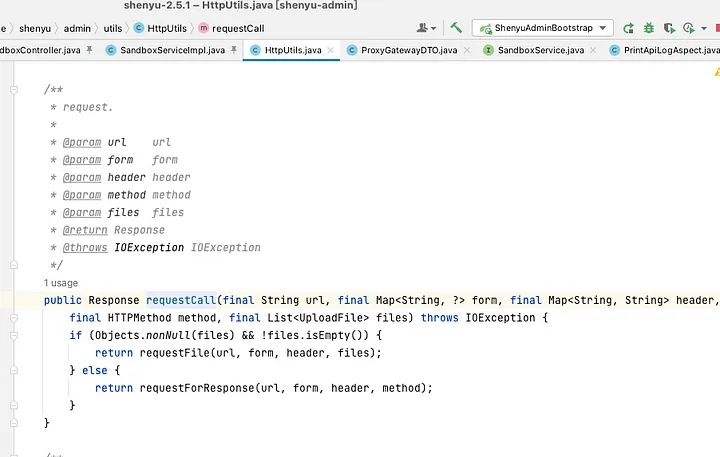
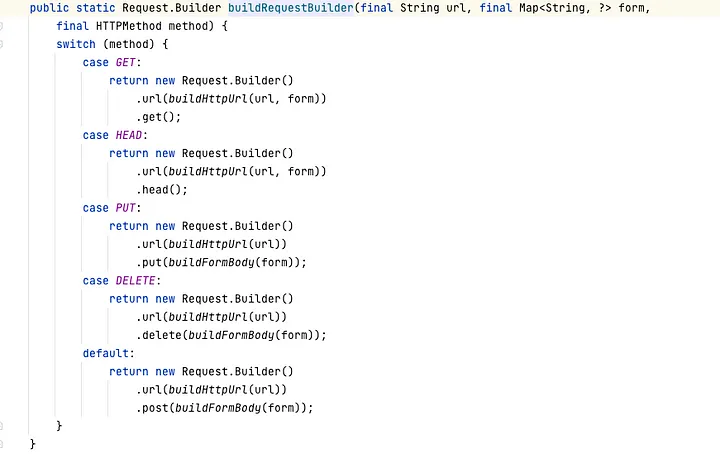
From the above flow you can see that there is no restriction on this request, we can use requestProxyGateway to utilize to send arbitrary http request as the URI, HTTP request method, header are all controllable.
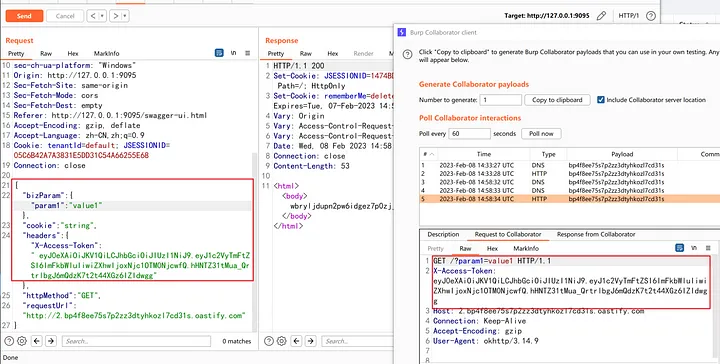
Attack Surfaces
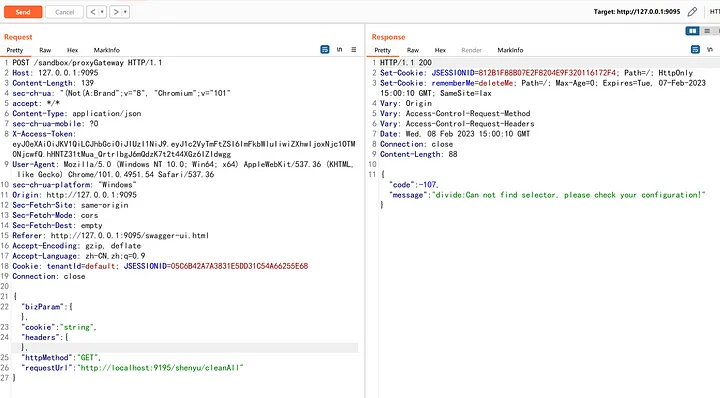
In addition to the usual SSRF exploitation methods, it is also possible to attack the local shenyu-bootstrap service on port 9195.
Fixes
Blacklist restrictions on ports have been made in the latest version!
Reference



