The incident occurred on August 10. Numen Cyber Labs, through on-chain transaction analysis and Twitter, found that the famous project Curve Finance was attacked. However, this attack is different from the common contract vulnerability attack or flash loan attack, instead, it was a DNS hijacking attack incident.
The Hacker visited the webpage of Curve. finance (https://curve.fi) and redirected to the malicious URL. Afterwards, the hacker placed a malicious attack contract on their page. So when the user authorized on the webpage, it was actually authorized to the contract address deployed by the hacker, and the hacker could directly transfer the money from the user’s wallet.
Till now, the hackers have obtained a total of $573,000 in assets on Ethereum.

Recently, security incidents are increasing, and hackers’ attack methods have emerged in an endless stream, so let’s also take a look at this attack incident (for example).
Hacker Address:
https://etherscan.io/address/0x50f9202e0f1c1577822bd67193960b213cd2f331
Attack Contract Address:
https://etherscan.io/address/0x9eb5f8e83359bb5013f3d8eee60bdce5654e8881
Transactions at the user authorization vulnerability address:
https://etherscan.io/tx/0xf63d9f7cc45395f3cfaaedadac14f86b0b0669c5314e0a23928c800c12fc5ad5
Transactions hackers transferring user address asset:
https://etherscan.io/tx/0x525fb894ed485b2cbdbdfaccedc3d405ba0f4659816ca4b639be7dd22e31a5e4
Attack Incident Analysis
Step 1:
Because DNS was hijacked by an attack, the Access Curve Finance webpage which user access was redirected to the malicious URL. So when the user authorizes the transaction, the authorisation is authorized to the hacker’s attack contract. And after authorisation, the user essentially becomes a lamb ready to be slaughtered by the hacker.
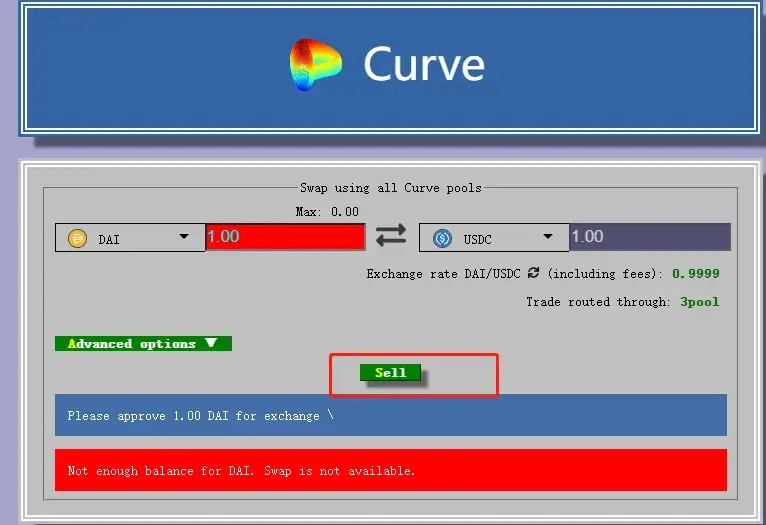
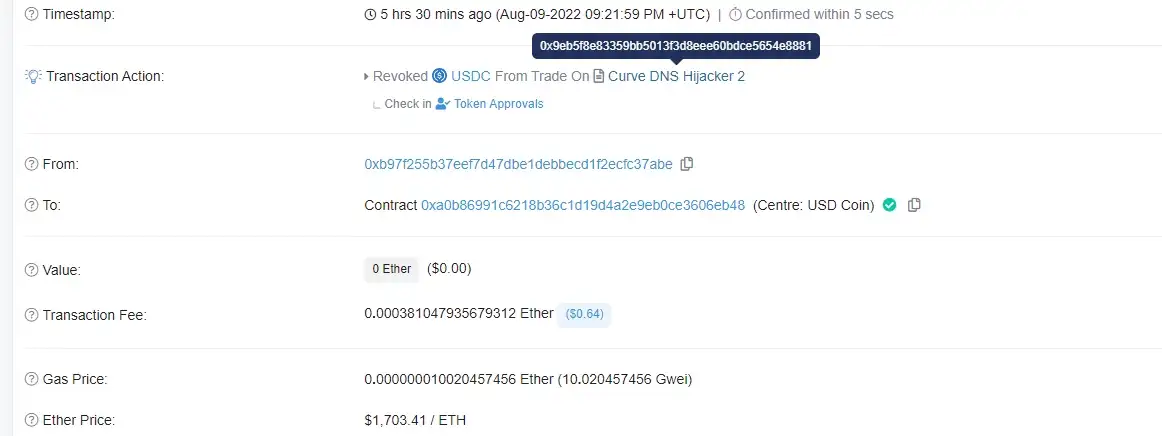
Step 2:
When the hacker contract address has the authorization of the user token, it can directly call the transfer function in the attack contract to transfer the tokens in the user’s wallet to the address specified by the hacker.
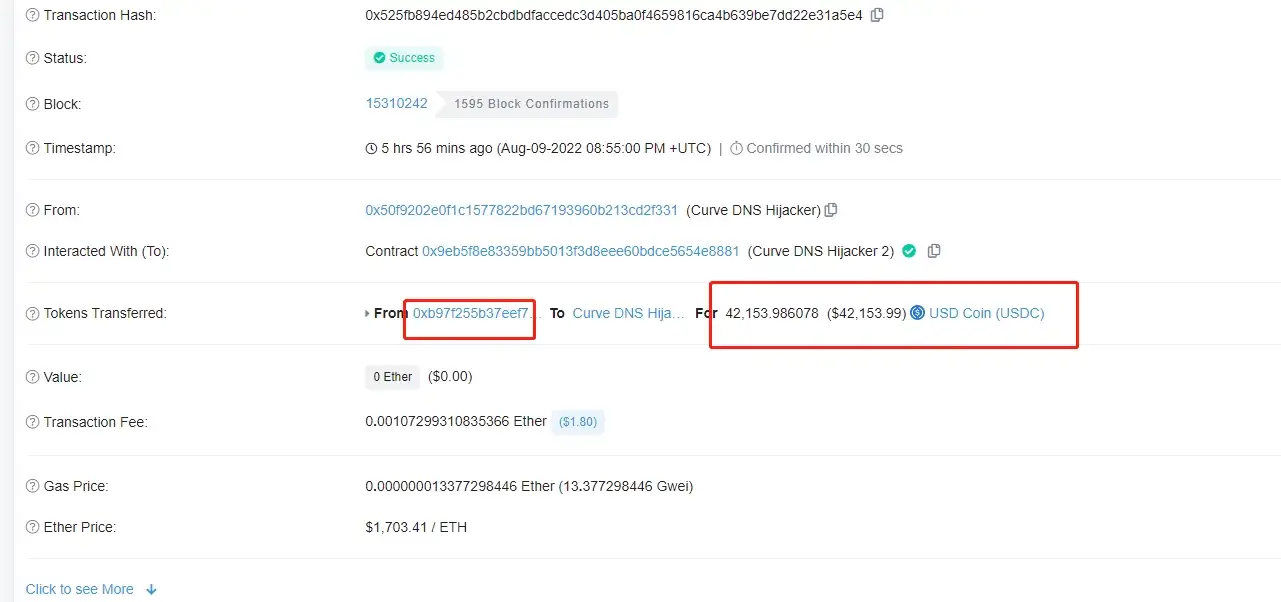
Step 3:
Hackers exchanged the tokens that profited from the attacks through some decentralized exchanges and transferred them through Tornado.Cash.
Conclusion
Currently, Curve officials also issued a notice that the problem has been found and restored, and it is recommended that users use https://curve.exchange/ethereum/, and DO NOT use https://curve.fi/ for the time being. They have reminded users that If they have approved any contracts on Curve in the past few hours to revoke the authorisation as soon as possible.
Should you wish to audit and ensure that your projects are free from exploits such as these, reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!
This blog was originally published on our Medium Account.


