
Smart contracts have become a popular way to manage digital assets and automate transactions on blockchain networks. However, as with any software, smart contracts are susceptible to vulnerabilities, and one of the most significant threats is the reentrancy attack. In this article, we’ll explore what reentrancy attacks are and how to prevent them to safeguard your smart contracts.
Understanding Reentrancy Attacks
A reentrancy attack is a type of vulnerability in smart contracts that allows attackers to execute a function multiple times before the previous call completes. This can lead to unexpected and harmful behavior, such as the theft of funds or unauthorized access to data.
There are currently three types of contract reentry that can be exploited by attackers: same method for the same contract, different methods for the same contract, and different methods for different contracts. It is important for developers to be aware of these types of vulnerabilities and take appropriate measures to prevent them in their smart contracts.
In a reentrancy attack, an attacker calls a function that interacts with another contract and then immediately calls the same function again before the first function call completes. This can exploit a flaw in the contract’s logic and allow the attacker to manipulate the contract’s state, causing significant damage.
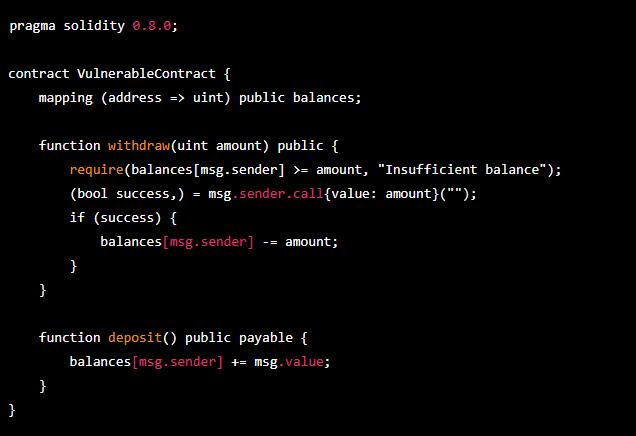
In the above smart contract, the withdraw function allows users to withdraw funds from their balance. The function first checks if the user has sufficient balance and then sends the requested amount to the user’s address. However, the function does not update the user’s balance before sending the funds, which can allow an attacker to exploit the reentrancy vulnerability.
An attacker can call the withdraw function multiple times in quick succession, triggering reentrancy. Each time the function is called, the attacker’s contract can call the withdraw function again before the previous call completes, allowing the attacker to drain the contract’s balance.
This is a vulnerability because the function does not update the user’s balance before sending funds, allowing an attacker to repeatedly call the function and drain the contract’s funds.
Preventing Reentrancy Attacks
Preventing reentrancy attacks is crucial to the security and reliability of smart contracts. Here are some best practices to prevent them:
1. Use Checks-Effects-Interactions Pattern
One way to prevent reentrancy attacks is to use the “checks-effects-interactions” pattern. This involves performing all checks and updating all state variables before interacting with other contracts. By performing checks first, developers can prevent unintended behavior by ensuring that the contract is in the expected state before continuing.
It’s important to pay special attention to the order of transfers and variable changes in deposit and withdrawal functions to ensure that they are executed in the correct sequence. Failure to do so can create opportunities for reentrancy attacks and other vulnerabilities
2. Use Mutex
Another approach to preventing reentrancy attacks is to use a mutex, which is a type of lock that prevents multiple calls to the same function from executing at the same time. By using a mutex, only one function call can be executed at any given time, preventing reentrancy attacks.
3. Smart Contract Auditing
Getting an audit of your smart contract from a reputable auditor can help identify potential vulnerabilities. This can be an effective way to identify and fix security flaws before they are exploited by attackers.
If you wish to ensure that your projects are free from potential reentrancy attacks, please reach out to us for an audit.
Conclusion
Reentrancy attacks pose a significant risk to smart contracts, and it’s essential to take all necessary precautions to prevent them. By using best practices such as the “checks-effects-interactions” pattern and mutexes, and getting an audit of your smart contract, you can help ensure the security and reliability of your blockchain-based applications.
Remember, always stay vigilant, be aware of the risks, and implement best practices to prevent reentrancy attacks in your smart contracts. Never take security for granted.


