
A smart contract audit is a comprehensive security review of a smart contract’s code and functionality. The purpose of the audit is to identify any potential security vulnerabilities or issues that could impact the contract’s ability to function as intended.
A smart contract is a self-executing contract with the terms of the agreement between buyer and seller being directly written into lines of code. They are immutable, transparent, and operate on blockchain technology, providing a secure and efficient way to facilitate transactions without the need for intermediaries.
However, with the increasing popularity and use of smart contracts, it has become increasingly important to ensure their security and reliability. This is where a smart contract audit comes into play.
Why are Smart Contract Audits Important?
A smart contract audit is crucial because it ensures the security and reliability of a smart contract. Smart contracts are immutable, meaning that once they are deployed on the blockchain, they cannot be changed. This makes it extremely important to ensure that they are secure and functioning as intended before they are deployed.
Smart contracts are integral to blockchain technology and are commonly used for transactions involving the transfer of funds. However, if a flaw exists within the code of a smart contract, it could potentially result in a system crash. Moreover, if a vulnerability is found in a smart contract that has already been deployed on the blockchain, it can be exploited, leading to financial losses.
This is why it’s crucial to conduct a security audit of a smart contract before deploying it onto the blockchain. A smart contract audit can help enhance the quality of the code, mitigate risks associated with smart contracts, and minimize the chances of being hacked.
Additionally, a smart contract audit can also help identify any potential performance bottlenecks, making it possible to optimize the contract’s code for better performance and efficiency.
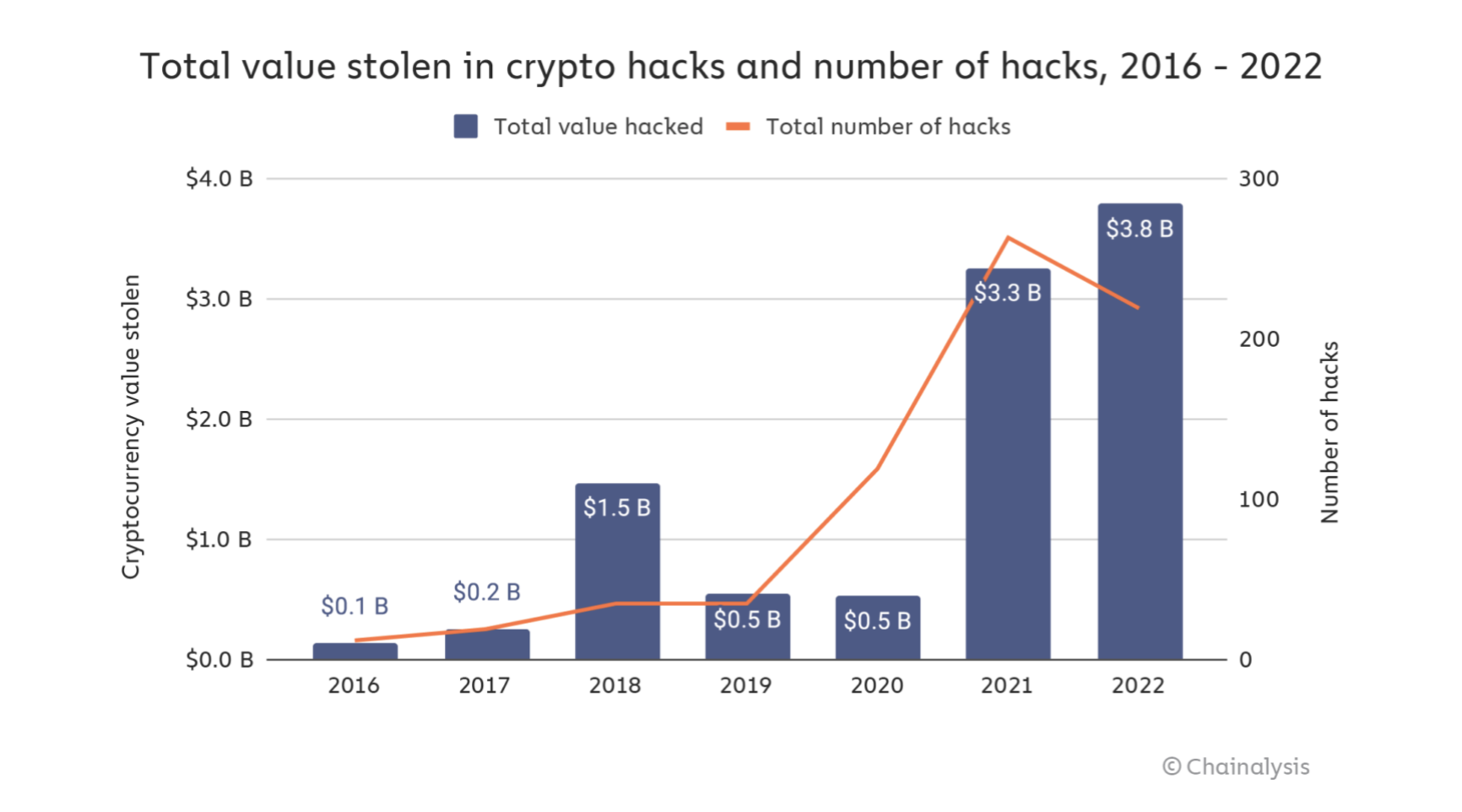
In 2022, the cryptocurrency industry experienced its largest-ever hacking activity, resulting in the loss of $3.8 billion from cryptocurrency businesses. DeFi Protocols suffered the most significant losses, with a total of $3.1 billion being stolen.
As a bridge becomes more prominent, any flaws in its underlying smart contract code or other vulnerable areas are likely to be discovered and taken advantage of by malicious actors.
This statistic is concerning, and project owners should be cautious about the possibility of their projects being targeted. Therefore, it’s crucial to conduct smart contract audits to ensure the security and integrity of the project.
How Do We Conduct a Smart Contract Audit?
A smart contract audit is typically conducted by a team of experienced blockchain developers and security experts. The team will review the contract’s code line by line, looking for any potential security vulnerabilities or issues that could impact the contract’s ability to function as intended.
The team will also test the contract’s functionality, simulating various scenarios and conditions to ensure that it operates as intended.
Step 1: Planning and Scoping
The first step in this process is to obtain the contract code from the client. Once the code is provided, the auditor must identify the appropriate audit content and consider any additional factors and documentation that may impact the audit process. This includes not only the contract codebase, but also the white paper and any other materials that may be related to the contract.
This includes collecting information on other contracts that may be related to the smart contract being audited, as well as the environments in which the contract operates. Additionally, it is important to identify any interaction components that may be involved in the contract audit process, as failure to do so may result in critical omissions that could lead to non-compliance with audit content.
Step 2: Code Review
To ensure the security and reliability of smart contracts, it is essential to conduct a comprehensive code review. This review can be done through deployment testing using tools such as Remix or test networks to familiarize the development team with the project’s smart contract and identify any possible security risks or bugs that may exist.
By conducting a thorough code review, the development team can facilitate subsequent audits and debug any contract risks that may have been missed during the development process. Performing this review prior to the audit ensures the effectiveness and efficiency of the auditing process.
Step 3: Testing with Tools
When conducting smart contract audits, it is essential to use multiple auditing tools to perform various types of risk scans. This approach helps to identify obvious security risks in the project’s smart contracts and manually identify any additional security risks that may have been missed during the development process.
By using a combination of auditing tools, auditors can identify a wider range of potential vulnerabilities, including code logic errors, overflow vulnerabilities, and permission issues. These tools help to ensure the reliability and security of smart contracts by detecting any potential risks before they can be exploited by malicious actors.
Step 4: Manual Testing
Once the auditors have become familiar with the project’s logic and have tested the smart contract code, a comprehensive manual audit is conducted. The first step is to rank the common risks associated with smart contracts, such as reentrancy vulnerabilities and access control issues.
The next step involves ranking the security risks that are specific to the project’s type, such as DeFi smart contract projects that may face lightning loan attacks or price manipulation risks.
Finally, threat modelling is used to determine the types of addresses interacting with the contract and ensure that there is no confusion about the interaction’s logic. These interactions are then ranked for risk to further improve the smart contract’s security.
Step 5: Propose Risk-Based Recommendations
In a smart contract audit project, risks are classified into different categories based on their potential impact and funding status. Recommendations for addressing each identified risk are provided, taking into consideration the risk’s level of hazard. Once the audit is completed, the project owner is informed of the security risk level and any recommended modifications.
In a smart contract audit project, risks can be categorized according to their level of severity or impact. The risk categories can vary:
- Critical: Risks that pose an immediate and significant threat to the system’s security and functionality, which could lead to significant financial losses or a complete system compromise.
- High: Risks that have a considerable impact on the system’s security and functionality, and could result in a significant loss of funds or a partial system compromise.
- Medium: Risks that could have a moderate impact on the system’s security and functionality, but may not result in a significant financial loss or system compromise.
- Low: Risks that have a minimal impact on the system’s security and functionality, and may not pose a significant threat to the system’s operations.
- Informational: Risks that do not necessarily pose an immediate threat to the system’s security and functionality, but could provide valuable information to stakeholders to enhance the system’s overall security posture.
Step 6: Audit Report Completion
Once the audit content and identified risks have been confirmed with the project, and the risks have been communicated to the project owner and reviewed, the smart contract audit report will be issued.
The report will include the audit findings, recommendations, and revisions made to address the identified risks. This step concludes the smart contract audit process and provides the project owner with valuable information to enhance the overall security and resilience of the smart contract.
If everything that might affect the integrity of the smart contract is fixed, the audit will be deemed to have passed.
Common Vulnerabilities and Exploits
Reentrancy
Reentrancy attacks are a type of smart contract vulnerability where the contract fails to properly handle the sequence of state changes when executing an external function call. Attackers exploit this by repeatedly calling and exiting the contract within a single transaction, maintaining the contract in a specific state, and stealing assets in the process.
Integer Overflow
A type of vulnerability that occurs during arithmetic operations when a variable exceeds the maximum value that can be represented by its data type, resulting in its value being reset to the minimum value or causing the calculation result to be incorrect. This can lead to unintended behavior in the smart contract and be exploited by attackers for malicious purposes.
tx.Origin
The Solidity global variable tx.origin returns the address of the original account that initiated a transaction. If an authorized account uses tx.origin for authorization and calls a malicious contract, the contract may be vulnerable to attacks. Malicious calls can bypass authorization checks by exploiting tx.origin to return the original sender of the transaction, which is the authorized account rather than the malicious contract.
Insecure Random Number
Insecure random number generation algorithms used in smart contracts can create security vulnerabilities, as attackers can predict the random number result in advance and use it to exploit the contract’s logic.
Price Manipulation
Price manipulation attacks, commonly known as “flash loan” attacks, occur when attackers take advantage of temporary price differences in a market to make a profit. In these attacks, the attacker uses a flash loan to borrow a large amount of cryptocurrency and then uses it to manipulate the price of a specific asset. This manipulation allows the attacker to make a profit by selling the asset at a higher price.
Replay Attack
A type of attack where an attacker maliciously re-sends a signed transaction to the network to repeat the transaction. In signing the transaction, the attacker is essentially reusing the transaction’s signature to gain access to sensitive data or steal funds.
How Long Does a Smart Contract Audit Take?
The duration of a smart contract audit depends on various factors, such as the complexity and amount of code within the project contract. The duration typically ranges from one to four weeks, but this can vary depending on the project’s specific requirements. The more complex the code, the longer the audit is likely to take.
If you’re interested in having your smart contract audited, please don’t hesitate to contact us. We’re always available to discuss your needs and provide professional assistance to ensure your smart contract’s security and integrity.


