On July 14th, the SpaceGodzilla project on BSC Chain has been hit by a flash loan attack. Hackers use flash loans to borrow large amounts of funds to manipulate the price of platform coins in the PancakeSwap trading pool and exploited the vulnerabilities in the project to attack. This attack hacker arbitraged 25,378.78BUSD. Numen Cyber Labs uncovered the secrets of the flash loans by analyzing the attack transaction and code details.

Event Analysis
Attacker wallet address:
https://bscscan.com/address/0x00a62eb08868ec6feb23465f61aa963b89e57e57
Attacker contract address:
https://bscscan.com/address/0x3d817ea746edd02c088c4df47c0ece0bd28dcd72
SpaceGodzilla token address:
https://bscscan.com/address/0x2287c04a15bb11ad1358ba5702c1c95e2d13a5e0
Attack transaction:
https://bscscan.com/tx/0x7f183df11f1a0225b5eb5bb2296b5dc51c0f3570e8cc15f0754de8e6f8b4cca4
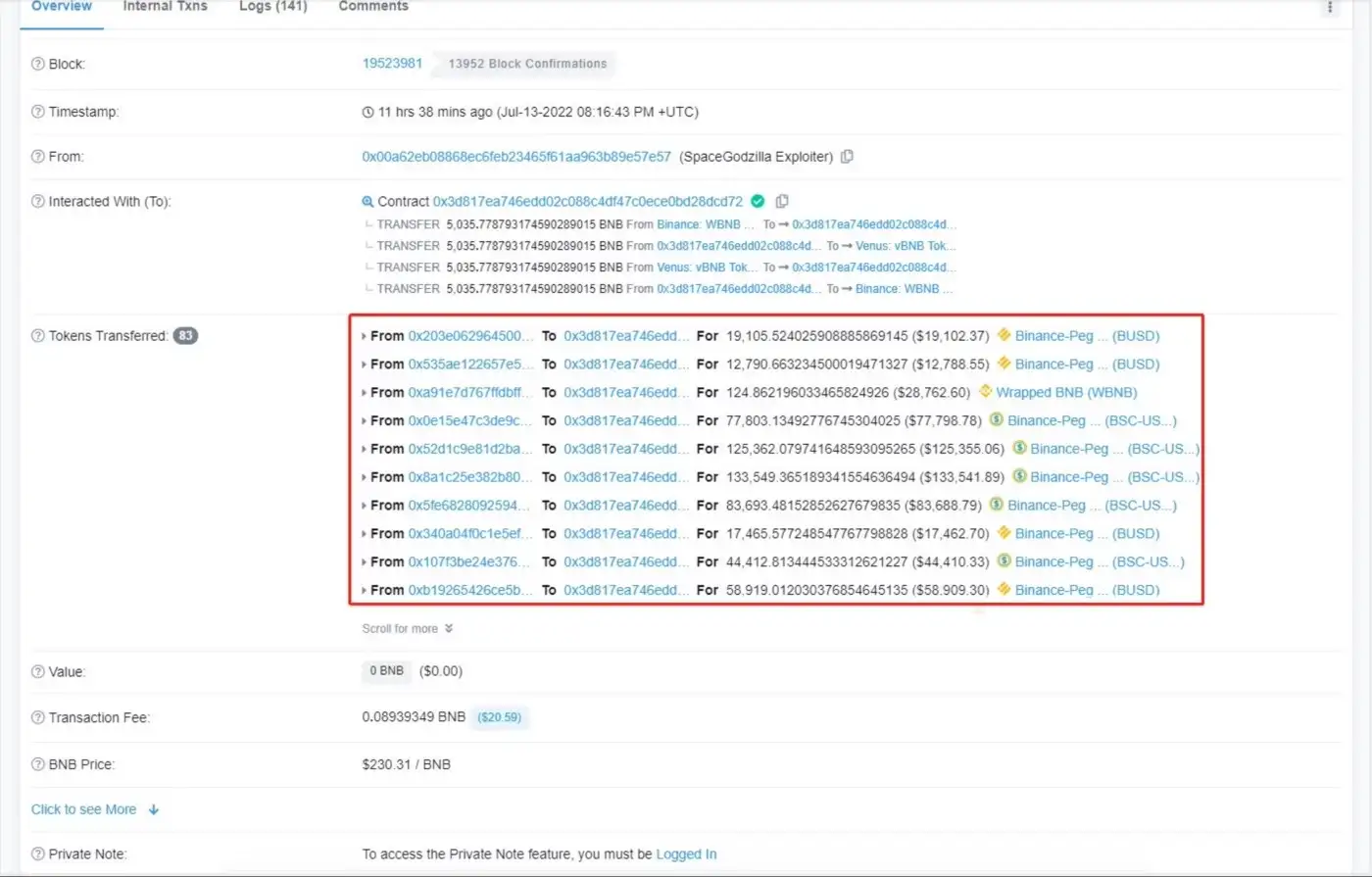
As shown in Figure 1, the attacker borrowed a large amount of BUSD, WBNB and other tokens from various lending platforms into the attack contract, and carried out some borrowing and swapping between tokens.
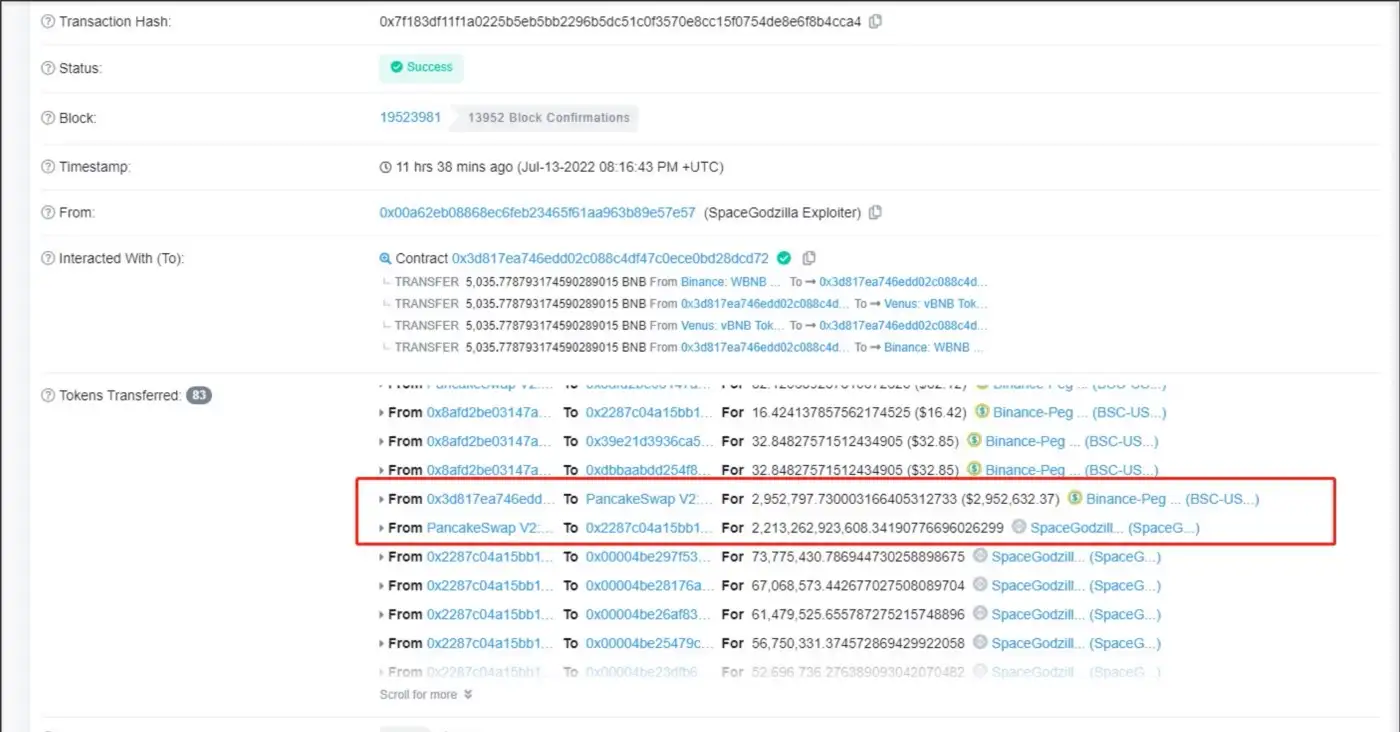
As shown in Figure 2 and Figure 3, the attacker exchanged the borrowed 2,952,797.73BUSD for 71,562,167,863,336 SpaceGodzilla tokens in the PancakeSwap transaction pool. As a result, the proportion of SpaceGodzilla and BUSD in the trading pool was affected, and the price of SpaceGodzilla was pulled up.
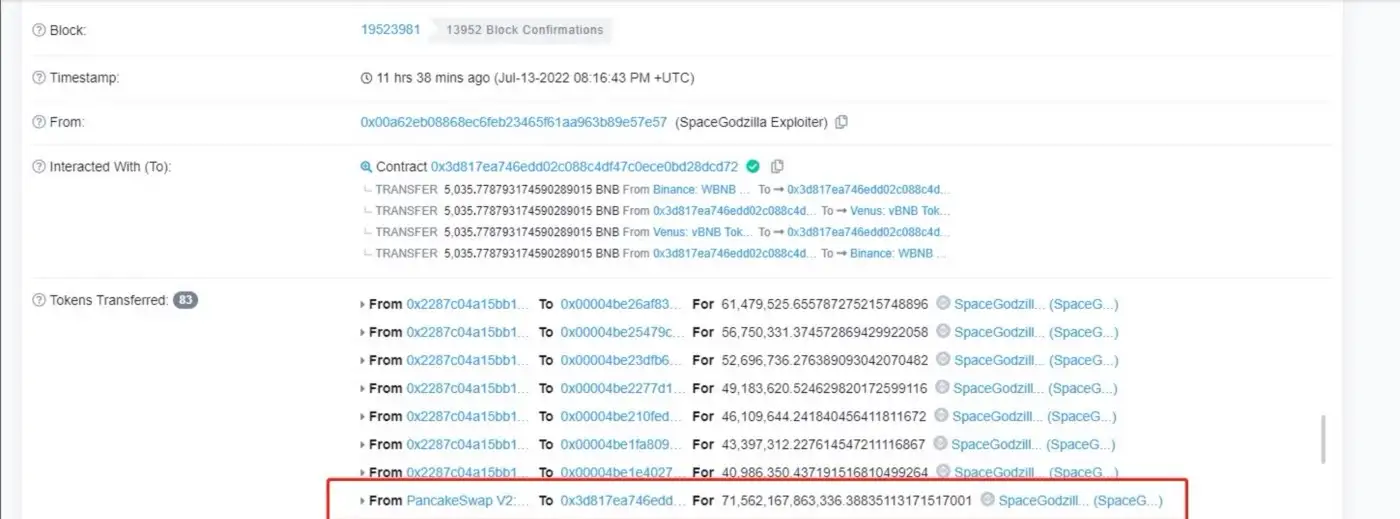
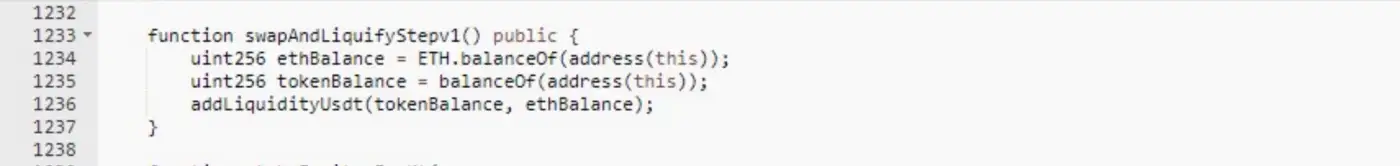
As shown in Figure 4 and Figure 5, The attacker called the swapAndLiquifyStepv1() function in the contract and added 30,395.26BUSD and 22,634,745,200.05 SpaceGodzilla under the current contract into the PancakeSwap trading pool. At this time, the proportion of the transaction pool is actually unbalanced.
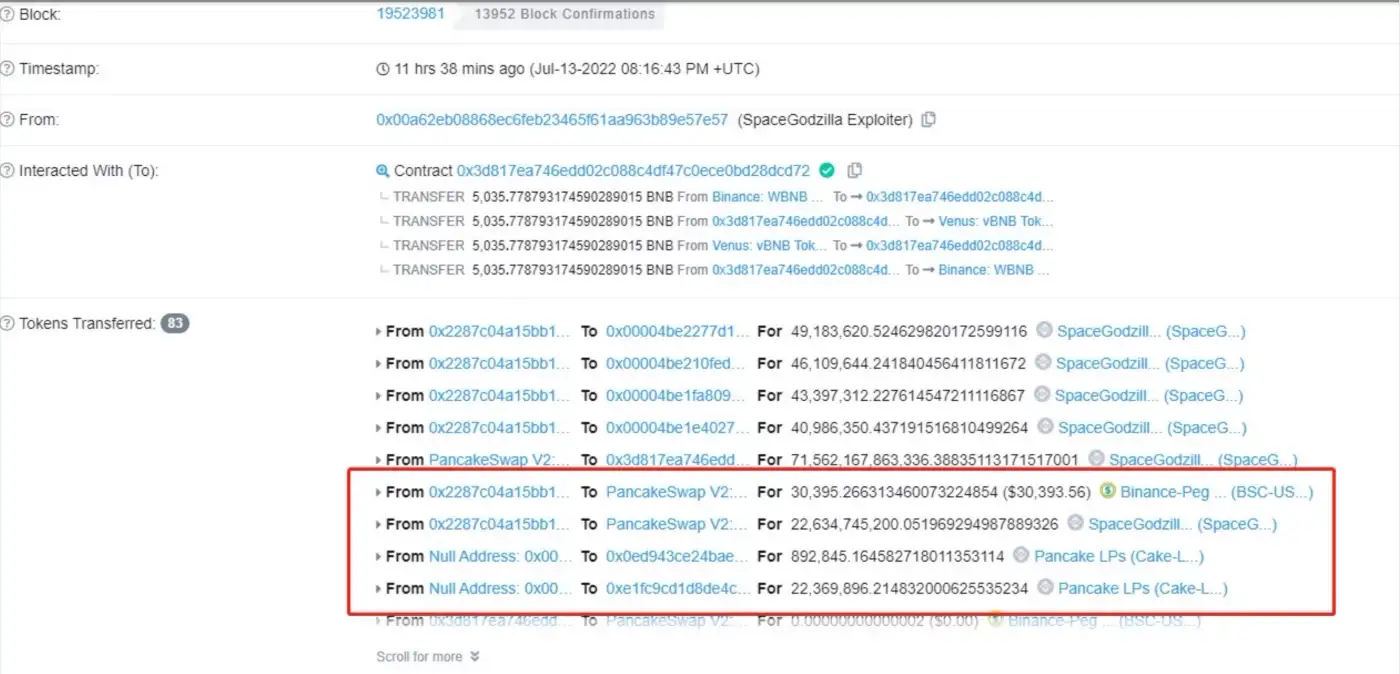
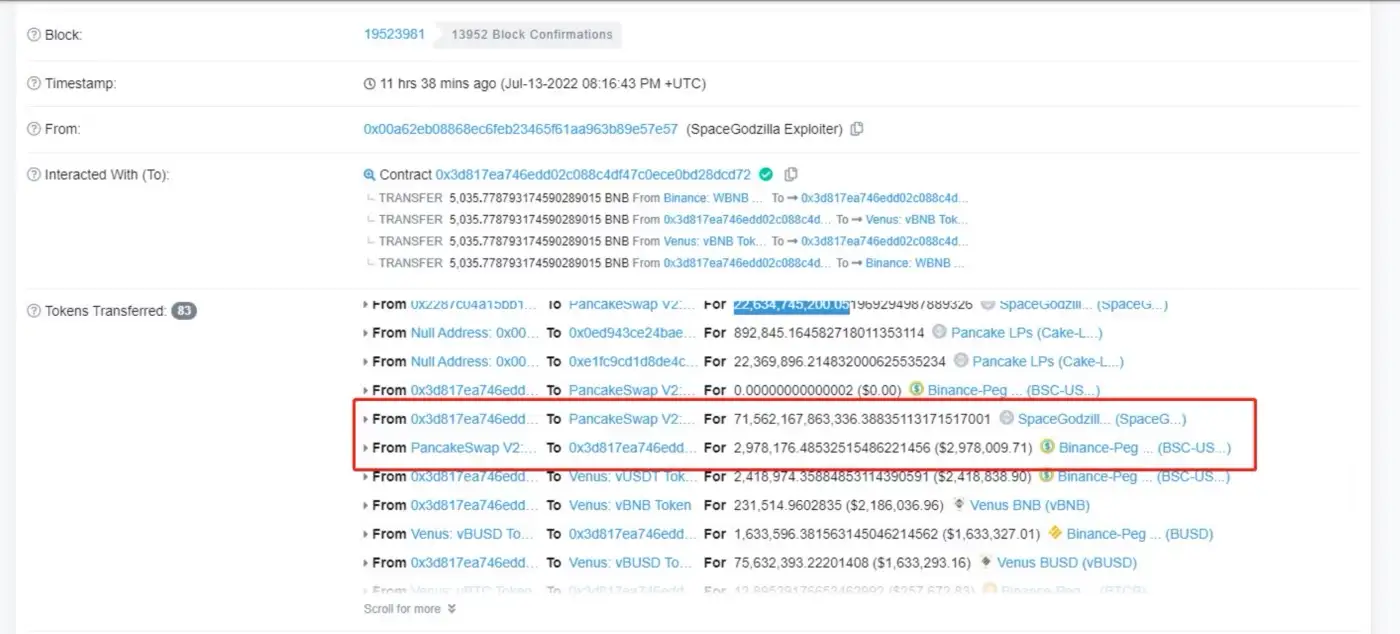
As shown in Figure 6, The attackers exchanged the previous 71,562,167,863,336 SpaceGodzilla tokens for 2,978,176.48 BUSD in the PancakeSwap trading pool. And returned the funds from the lending platform, the hacker made a profit of 25,378.78BUSD.
Summary
From Figure 7 we can see, presently, the hacker has exchanged the 25,378.78BUSD profited from this attack to BNB, which is transferred via Tornado.Cash. The reason for this attack is that there are certain security vulnerabilities in the code logic of the project. The swapAndLiquifyStepv1() function adds both tokens under the contract to the trading pool of PancakeSwap when adding liquidity.
At this time, the proportion of the transaction pool is unbalanced, thus giving the chance to hackers exploiting this vulnerability to attack. Numen Cyber Labs recommend that all functions connected to the DEX interface in all projects must be rigorously tested.
Should you wish to audit and ensure that your projects are free from exploits such as these, reach out to us here.
Numen Cyber Labs is committed to facilitating the safe development of Web 3.0. We are dedicated to the security of the blockchain ecosystem, as well as operating systems & browser/mobile security. We regularly disseminate analyses on topics such as these, please stay tuned or visit our blog here for more!
This blog was originally published on our Medium Account.


